Java Anon ProxyJonDonym also known as Java Anon Proxy (JAP), is the proxy system that is made to allow Web browsing with the revocable pseudonymity (the state of using or being published under a pseudonym, a false or fictitious name). Without this anonymity, every device that is using the internet use a traceable address, i.e.:
Can find out which sites are being surfed by the user or what kind of request is being done on a particular system if the encryption is not used. However, in JAP neither any eavesdropper nor any visited site can find out what sorts of request is being made by the user, as JAP uses a static address that is being shared by other JAP users. Working of Java Anon ProxyWhen Java Anon Proxy is used, the user does not get connected to a requested site directly. In fact, the user takes a long route for connecting to the site. The long route consists of the connection with encryption through different intermediaries, knows as Mixes. A predetermined sequence is being used by the JAP for Mixes. The kind of sequence of the linked mixes is known as the Mix Cascade. Users are allowed to choose between different mix cascades. To achieve the long route, it is required to configure the web browser so that data travels through the JAP first instead of going to the requested site directly. 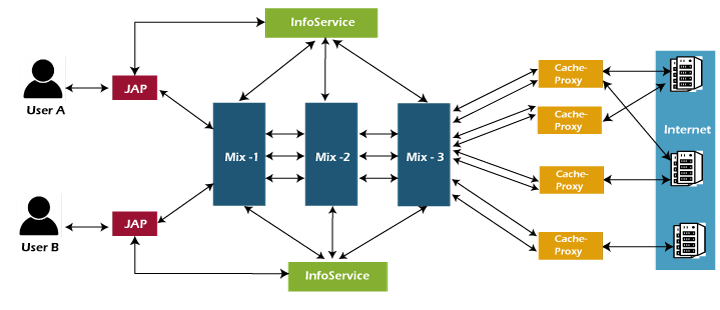
When a user starts the JAP software, the JAP first establishes a connection with the InfoService to ensure that the program version is still compatible. If the version of the JAP software is not compatible with the software of the mix, the user is asked to update the program; otherwise, it is not possible to use the JAP service. The next step consists of the JAP registering with the first mix station of the chosen mix cascade. The network connection between the JAP program and the first mix station is permanent until logoff. Encryption in Java Anon ProxyThe encryption of data is first done by the JAP software. The encrypted data is then sent to the first mix station. The first mix station mixes the encrypted data with the data of other users, and then the data is received by the second mix station. The second mix station then transfers the data to the third mix where decryption occurs, and then the data is sent to the internet via the cache proxy, as shown in the above diagram. JAP utilizes strong encryption between the client's system and the other JAP servers. As stated above that multiple encryptions of data happen. One can think of it as an onion-like structure because of multiple layers of encryption. A layer of encryption surrounds the data for the last mix in the mix cascade. Only the last mix can take out this layer to fetch the data. Another layer of encryption is put around the already encrypted data for the second to the last mix. In a similar fashion, the third layer of encryption happens for the third to the last mix. Types of Encryptions in Java Anon ProxyJava Anon Proxy uses the asymmetrical cryptographic process to do the encryption so that each layer of encryption is only getting removed by the appropriate mix. The Asymmetrical cryptographic processes are discriminated by their usage of the two keys - one secret key that is utilized to decrypt the encrypted data, and the other is the publicly known key that is used to perform the encryption of data. The secret key is the key that is known only by the specific mix station by which the encrypted data is supposed to be decrypted. Following are the two encryption methods used by the Java Anon Proxy.
To have a higher efficiency, the data is symmetrically encrypted with the AES. The slower asymmetric RSA method does the encryption of the symmetric key. Benefits of EncryptionThere are two important reasons why encryption is very important to achieve anonymization. 1) To ensure that encrypted data are getting decrypted in the proper way by the real mixes and not from any eavesdropper or attacker. 2) The encryption at different layers makes data more secure, as the data looks different every time when it is encrypted. Thus, it becomes extremely difficult for an attacker to establish a connection between the outgoing and incoming message based on how the data look. Cons of Java Anon ProxyFollowing restrictions should be taken into consideration to allow the anonymity of the user. 1) An attacker should never control the mix present in the cascade. 2) The attacker should never control the other users. It is because the attacker knows the data coming from the others. Therefore, the extra data that is coming must be coming from the real user and not from the mix. Hence, an attacker can target the user easily.
Next TopicKnapsack Problem Java
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










