Java Code for DESOur dependency on the internet is increasing day by day and we share lots of personal information with others. Since our data or personal information is not secure. For this reason, the security of the data become essential for us. We need to keep data confidential, unmodified, and readily available to authorized readers only. We can make secure data by using the DES (Data Encryption Standard) mechanism that can encrypt and decrypt the data. Using the DES algorithm is the most popular way to encrypt and decrypt data. It is a widely used symmetric (encryption and decryption) algorithm in the world. In this section, we will learn the DES algorithm that is used to generate the ciphertext. Also, we will implement the DES algorithm in a Java program. 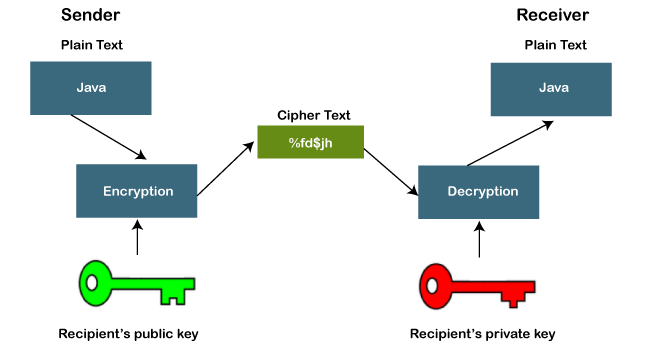
DES AlgorithmDES stands for Data Encryption Standard. It is a symmetric-key block cipher algorithm used to encrypt and decrypt data. It is developed by the IBM team in early 1970. It accepts the plaintext in 64-bit blocks and changes it into the ciphertext that uses the 64-bit keys to encrypt the data. The algorithm uses the same key to encrypt and decrypt the data. It is based on LUCIFER (also known as Feistel block cipher algorithm) which is a direct predecessor of the DES algorithm. It is developed by eminent scholar and researcher Horst Feistel at IBM. It provides high security by using a 128-bit key block and a 128-bit block size. The DES algorithm uses the 16 rounds of the Feistel structure. The structure uses a unique key for each round. Finally, in 1976, it was approved by the federal encryption standard. In 2002, AES (Advanced Encryption Standard) replaced the DES encryption algorithm as the accepted standard. Later in 1995, the advanced version of the DES algorithm was introduced that is known as Triple DES (3DES or TDES). Officially, it is known as Triple Data Encryption Algorithm (TDEA or 3DEA). TDEA is also a symmetric-key block cipher algorithm that uses the DES cipher algorithm thrice to each data block. Its block size is 64-bits and key sizes are 168, 112, and 56-bits, respectively for the keys 1, 2, and 3. It also uses the DES equivalent rounds i.e. 48. It means 16 rounds for each key. 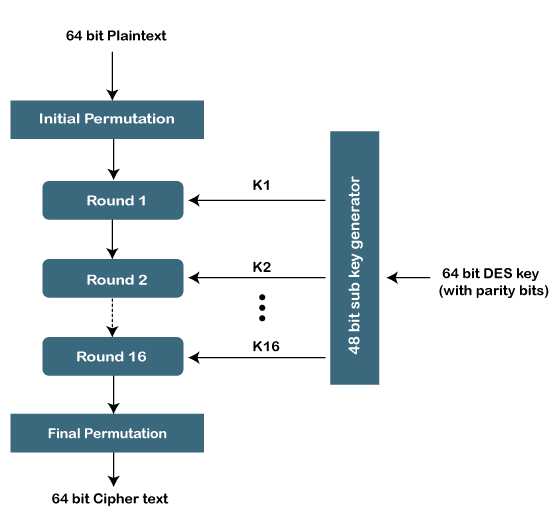
It encrypts the data using the first key (k1), decrypts the data by using the second key (k2) and again encrypts the data by using the third key (k3). Another variant of the algorithm uses only two keys k1 and k3. Where both the keys k1 and k3 are the same. It is used still but considered as a legacy algorithm. The following figure shows the encryption and decryption using TDEA. 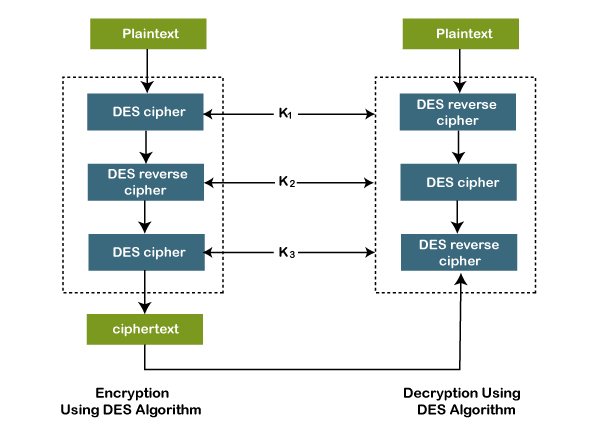
Let's understand the DES algorithm. Generating KeysThe algorithm performs 16 rounds of encryption and for each round, a unique key is generated. Before moving to the steps, it is important to know that in plaintext the bits are labeled from 1 to 64 where 1 is the most significant bit and 64 is the least significant bit. The process of generating keys are as follows: 1. First, we compress and transpose the given 64-bit key into a 48-bit keys by using the table given below: 2. Separate the result into two equal parts i.e. C and D. 3. The part C and D are left-shifted circularly. For encryption, the 1st, 2nd, 9th, and 16th round is responsible that shifts a bit to the left by 1 bit, circularly. All the rest rounds are shifted to the left by 2-bit circularly. 4. After that, the result is compressed to 48-bits with the help of the following table. 5. The result that we get from step 3 becomes the input for the next round of the key generation. Encryption Steps of the AlgorithmThe algorithm includes the following steps:
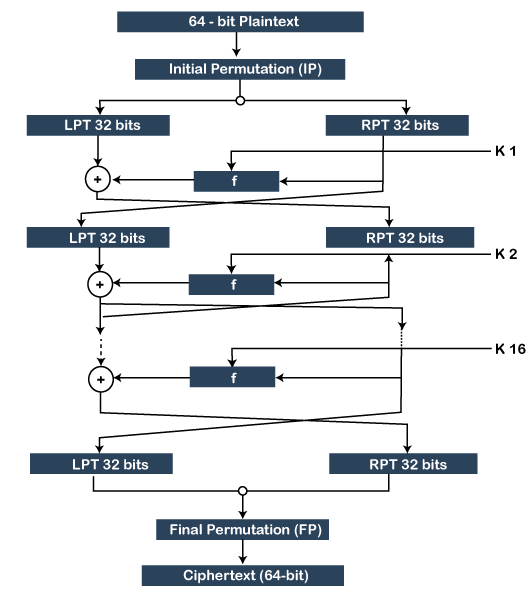
Decryption Step of the AlgorithmFor decryption of the ciphertext, we use the same algorithm but in reverse order (step 4) of 16 round keys. For better understanding of the algorithm, let's see modes of operation for the DES algorithm. Modes of Operation For DESThere are the following five modes of operation that can be chosen:
We conclude that the basic steps of the algorithm are:
Let's implement the DES algorithm in a Java program and see how data is encrypted and decrypted using the algorithm. DesProgram.java Before running the above program, you will have to do some changes in the program. First, you will have to create a text file that you want to encrypt. In our case, we have created a file with the name DemoData.txt and written the following text into it. You can write anything. DemoData.txt 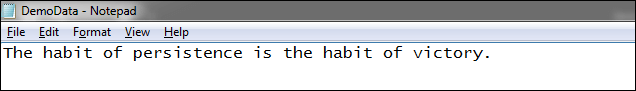
Let's run the above program and see the output. Output: 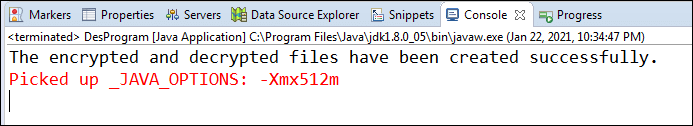
When we run the above program, it generates the two files encrypteddata.txt and deecrypteddata.txt at the specified location. Let's see what inside the encrypted and decrypted file. encrypteddata.txt 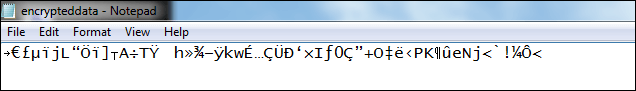
deecrypteddata.txt 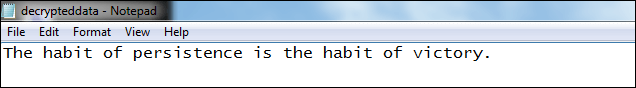
We see that data is decrypted into the same text as we had written in the DemoData.txt file.
Next TopicPig Latin Program in Java
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










