Mobile IPThis is an IETF (Internet Engineering Task Force) standard communications protocol designed to allow mobile devices' (such as laptop, PDA, mobile phone, etc.) users to move from one network to another while maintaining their permanent IP (Internet Protocol) address. Defined in RFC (Request for Comments) 2002, mobile IP is an enhancement of the internet protocol (IP) that adds mechanisms for forwarding internet traffic to mobile devices (known as mobile nodes) when they are connecting through other than their home network. 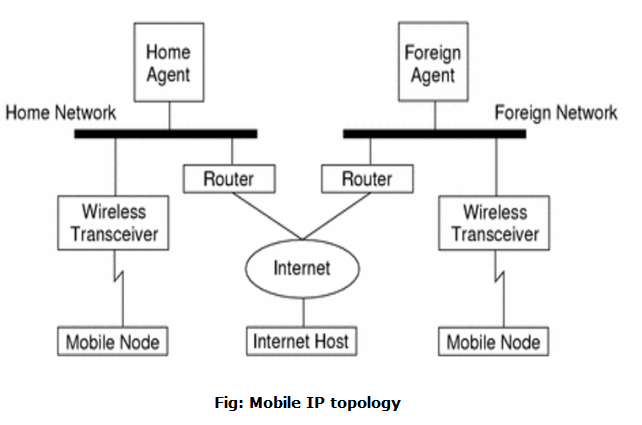 The following case shows how a datagram moves from one point to another within the Mobile IP framework.
In the case of wireless communications, the above illustrations depict the use of wireless transceivers to transmit the datagrams to the mobile node. Also, all datagrams between the Internet host and the MN use the mobile node's home address regardless of whether the mobile node is on a home or foreign network. The care-of address (COA) is used only for communication with mobility agents and is never seen by the Internet host. Components of Mobile IPThe mobile IP has following three components as follows: 1. Mobile Node (MN)The mobile node is an end system or device such as a cell phone, PDA (Personal Digital assistant), or laptop whose software enables network roaming capabilities. 2. Home Agent (HA)The home agent provides several services for the mobile node and is located in the home network. The tunnel for packets towards the mobile node starts at home agent. The home agent maintains a location registry, i.e. it is informed of the mobile node's location by the current COA (care of address). Following alternatives for the implementation of an HA exist.
3. Foreign Agent (FA)The foreign agent can provide several services to the mobile node during its visit to the foreign network. The FA can have the COA (care or address) acting as a tunnel endpoint and forwarding packets to the MN. The foreign agent can be the default router for the MN. Foreign agent can also provide security services because they belong to the foreign network as opposed to the MN which is only visiting. In short, FA is a router that may function as the point of attachment for the mobile node when it roams to a foreign network delivers packets from the home agent to the mobile node. 4. Care of Address (COA)The Care- of- address defines the current location of the mobile node from an IP point of view. All IP packets sent to the MN are delivered to the COA, not directly to the IP address of the MN. Packet delivery toward the mobile node is done using a tunnel. To be more precise, the COA marks the endpoint of the tunnel, i.e. the address where packets exit the tunnel. There are two different possibilities for the location of the care of address:
5. Correspondent Node (CN)At least one partner is needed for communication. The correspondent node represents this partner for the MN. The correspondent node can be a fixed or mobile node. 6. Home NetworkThe home network is the subset the MN belongs to with respect to its IP address. No mobile IP support is needed within this network. 7. Foreign networkThe foreign network is the current subset the MN visits and which is not the home network. Process of Mobile IPThe mobile IP process has following three main phases, which are: 1. Agent DiscoveryDuring the agent discovery phase the HA and FA advertise their services on the network by using the ICMP router discovery protocol (IROP). Mobile IP defines two methods: agent advertisement and agent solicitation which are in fact router discovery methods plus extensions.
2. RegistrationThe main purpose of the registration is to inform the home agent of the current location for correct forwarding of packets. 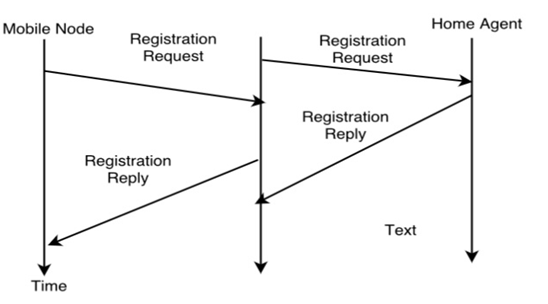 Registration can be done in two ways depending on the location of the COA.
Additionally, the mobility biding contains the lifetime of the registration which is negotiated during the registration process. Registration expires automatically after the lifetime and is deleted; so a mobile node should register before expiration. After setting up the mobility binding, the HA send a reply message back to the FA which forwards it to the MN.
3. TunnelingA tunnel is used to establish a virtual pipe for data packets between a tunnel entry and a tunnel endpoint. Packets which are entering in a tunnel are forwarded inside the tunnel and leave the tunnel unchanged. Tunneling, i.e., sending a packet through a tunnel is achieved with the help of encapsulation. Tunneling is also known as "port forwarding" is the transmission and data intended for use only within a private, usually corporate network through a public network. Next TopicDynamic Host Configuration Protocol |