Segmentation Fault Core Dumped UbuntuWhat is a Segmentation Fault?Segmentation Fault or access violation (segfault in short) is a failure condition or fault that is arisen by hardware with memory protection, alerting an operating system the software has attempted for accessing a restricted memory area (a memory access violation). It is a general protection fault form on standard x86 systems. In response, the kernel of the operating system will usually implement a few corrective operations, generally passing that fault on to the offending process by transferring a signal to the process. In some cases, processes can install a signal handler, permitting them for recovering on their own, but otherwise, the default signal handler of the operating system is used, generally leading to the process's abnormal termination, and a core dump sometimes.
Overview of Segmentation Fault
Causes of Segmentation FaultThe circumstances under which a segmentation fault appears and how it manifests itself are specific to the operating system and hardware. Different hardware arises different faults for several circumstances and different operating systems transform these into different signals that are sent to the processes. The forthcoming cause can be a memory access violation, although the underlying cause is a software bug of a few sorts. Debugging a bug or deciding the root cause can be easy in a few cases, in which the program will lead to a segmentation fault consistently. However, the bag could be difficult for reproducing and rely on the memory allocation on every run in other cases. The following are a few typical causes of the segmentation fault:
Segmentation faults often appear due to the errors in the use of a pointer, specifically in C dynamic memory allocation in C code. Dereferencing to a null pointer, which outcomes in undefined behavior, will lead to a segmentation fault. It is due to a null pointer that can't be a valid memory address. The dangling pointers and wild pointers indicate a memory that might or might not exist and might or might not be writable or readable and thus can outcome in transient bugs. Resolve segmentation fault in UbuntuThis error might strike our Ubuntu system at any point. Segmentation fault is when our system attempts to access any page of memory that does not exist. Core dumped defines when a code part attempts to perform a write and read operation on a free or read-only location. Generally, segfaults are associated with a file named core and happen at the time of up-gradation. While executing a few commands at the time of the core dump situation we might encounter the "Unable to open lock file" error. It is due to the system is attempting to take a bit of block that is not existing. It is because of the crashing of binaries of a few specific programs. We may be debugging or backtracking for resolving it but the solution is to fix the broken packages by implementing some steps which are mentioned as follows: 1. Remove the lock files available at distinct locations. 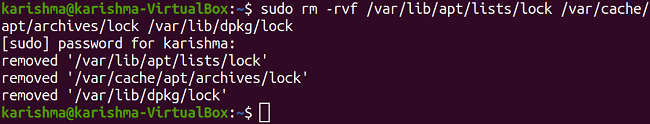 2. Removing repository cache.  3. Upgrade and update our repository cache. 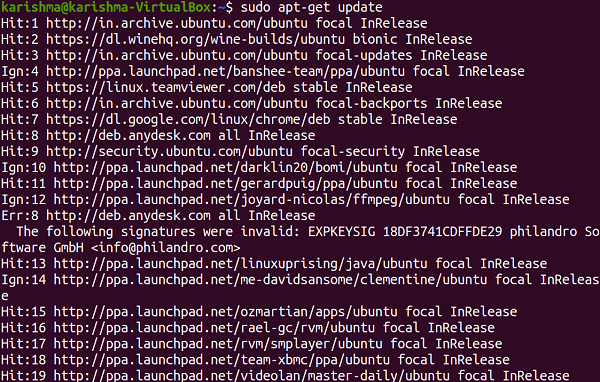 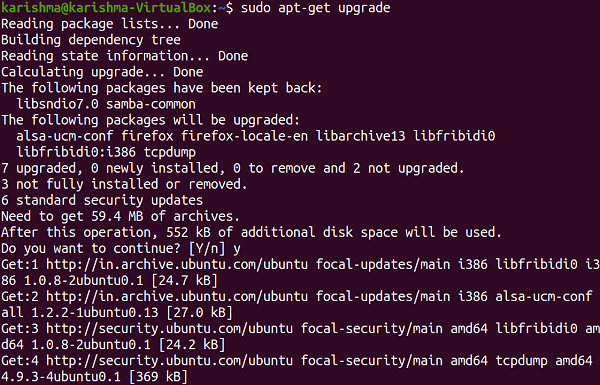 4. Now upgrade our distribution it will update our packages. 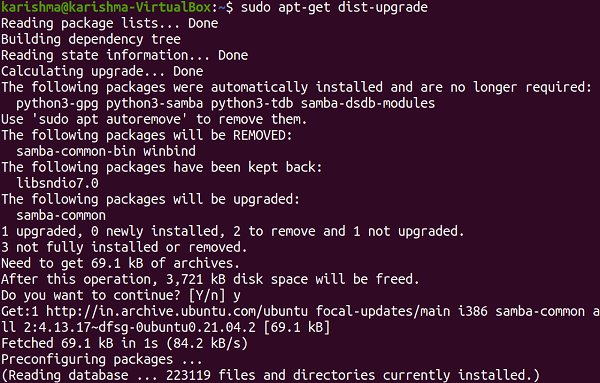 5. Search the broken packages and remove them forcefully. A great way which always will work is as follows apart from the command line:
Now, we have two ways to resolve segmentation fault GUI and CLI. Sometimes, it might also happen that the command, i.e., apt is not working due to the segfault, so the CLI method will not implement. In that situation, do not worry because the GUI method will always work for us. Handling Segmentation FaultThe default task for a bus error or segmentation fault is the abnormal termination of a process that encountered it. A core file might be produced to help to debug, and other platform-dependent tasks might also be implemented. For example, many Linux systems applying the grsecurity patch might log SIGSEGV signals for monitoring for possible intrusion attempts with buffer overflows. On a few systems, like Windows and Linux, it is possible for a program itself to manage a segmentation fault. The running program can't only manage the event but might extract a few details about its status like the values of processor register, getting a stack trace, the line of a source code when it was encountered, memory address that was accessed invalidly, and whether the task was a write or a read depending on the operating system and architecture. However, a segmentation fault defines that a program has an error that requires fixing, it's also possible to cause such failure intentionally for the testing purpose, debugging, and also to imitate platforms in which direct access is required to memory. The system should be able to permit the program to execute even after the error occurs in the latter case. In this situation, when the system permits, it's possible to manage the event and enhance the processor program counter to "jump" on the failing instruction to proceed with the execution. Examples of segmentation fault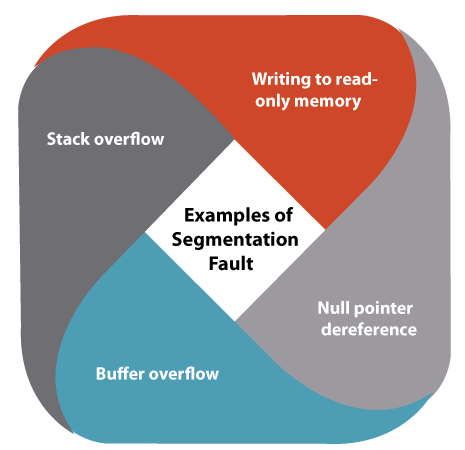 Writing to read-only memoryIt arises a segmentation fault. It appears when the program writes to a part of its code segment or the read-only part of the data segment at the code error levels because these are loaded via the operating system into the read-only memory. Null pointer dereferenceIn C and other C-like languages, the null pointers are used for meaning "pointer to no object" and as the error indicator and dereferencing in the null pointer (a write or read from a null pointer) is a very basic program error. The standard doesn't say that the null pointer is similar to the pointer to 0 memory address, though that might be the case. Almost all operating systems map the address of the null pointer such that using it leads to a segmentation fault. This behavior is not guaranteed by any C standard. In C, dereferencing the null pointer is the undefined behavior, and a conforming implementation is permitted to assume that a pointer that's dereferenced isn't null. Buffer overflowStack overflowNext TopicSpotify Ubuntu |