DCL Commands in SQL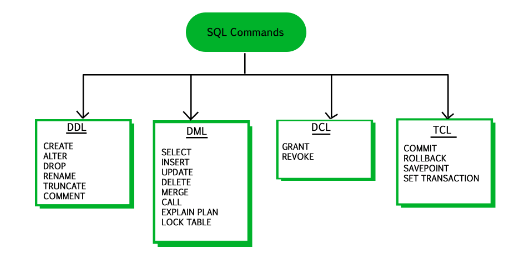
DCL is an abbreviation for Data Control Language in SQL. It is used to provide different users access to the stored data. It enables the data administrator to grant or revoke the required access to act as the database. When DCL commands are implemented in the database, there is no feature to perform a rollback. The administrator must implement the other DCL command to reverse the action.
Types of DCL Commands in SQLTwo types of DCL commands can be used by the user in SQL. These commands are useful, especially when several users access the database. It enables the administrator to manage access control. The two types of DCL commands are as follows:
GRANT CommandGRANT, as the name itself suggests, provides. This command allows the administrator to provide particular privileges or permissions over a database object, such as a table, view, or procedure. It can provide user access to perform certain database or component operations. In simple language, the GRANT command allows the user to implement other SQL commands on the database or its objects. The primary function of the GRANT command in SQL is to provide administrators the ability to ensure the security and integrity of the data is maintained in the database. To have a better understanding of implementing the GRANT statement in the database. Let us use an example. Implementing GRANT StatementConsider a scenario where you are the database administrator, and a student table is in the database. Suppose you want a specific user Aman to only SELECT (read)/ retrieve the data from the student table. Then you can use GRANT in the below GRANT statement. This command will allow Aman to implement the SELECT queries on the student table. This will enable the user to read or retrieve information from the student table. Note: Implementing the above statement will also limit Aman's operations. Aman won't be able to modify the data stored in the table. It will prevent the user from user to insert, to update, or deleting the data in the student table in the database.REVOKE CommandAs the name suggests, revoke is to take away. The REVOKE command enables the database administrator to remove the previously provided privileges or permissions from a user over a database or database object, such as a table, view, or procedure. The REVOKE commands prevent the user from accessing or performing a specific operation on an element in the database. In simple language, the REVOKE command terminates the ability of the user to perform the mentioned SQL command in the REVOKE query on the database or its component. The primary reason for implementing the REVOKE query in the database is to ensure the data's security and integrity. Let us use an example to better understand how to implement the REVOKE command in SQL. Implementing REVOKE CommandConsider a scenario where the user is the database administrator. In the above implementation of the GRANT command, the user Aman was provided permission to implement a SELECT query on the student table that allowed Aman to read or retrieve the data from the table. Due to certain circumstances, the administrator wants to revoke the abovementioned permission. To do so, the administrator can implement the below REVOKE statement: This will stop the user Aman from implementing the SELECT query on the student table. The user may be able to implement other queries in the database. Benefits of Implementing DCL CommandsThere are several advantages of implementing Data Control Language commands in a database. Let's see some most common reasons why the user implements DCL commands on the database.
Disadvantages of Implementing DCL CommandsAlong with the benefits of implementing DCL commands in the database, they have some disadvantages. Some of the common disadvantages of implementing DCL commands are as follows:
Next TopicSQL Limit
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










