Layered Architecture in Computer Networks
In this article, we will discuss about layered architecture, a vital idea in computer networks.
Modern verbal exchange structures are supported by computer networks, which permit the frictionless transmission of data and data throughout borders. Network architects utilise a layered architectural technique to promote powerful and dependable conversation. This fundamental shape, commonly called the OSI (Open Systems Interconnection) model, organises networking functions into numerous layers, each with a separate feature and set of obligations. In this deep exam, we explore the technical aspects of layered structure in computer networks and its ancient development, significance, and realistic packages.
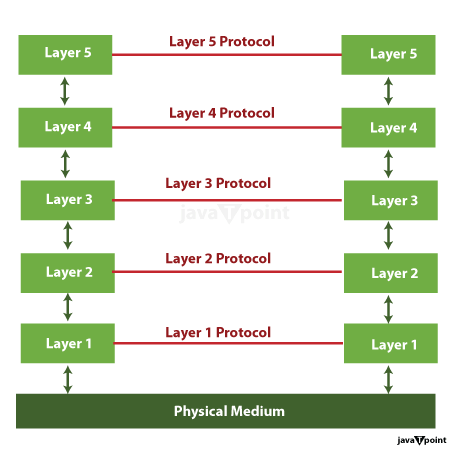
Understanding Layered Architecture
An architectural method known as "layered structure" in computer networks separates the networking stack into various degrees, each at the price of a one-of-a-kind verbal exchange feature. This modular method simplifies network layout and protection by dividing hard jobs into workable components. The OSI version, which has seven stages, is the most widely used layered architectural reference:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
Each layer plays essential responsibilities and interacts with decreased layers using standard interfaces to encourage interoperability between network gadgets and technology.
Significance of Layered Architecture
Layered architecture gives several blessings to computer networks:
- Modularity: The community stack may be divided into layers so that every layer can be one after the other planned, carried out, and maintained. This modularity allows network setting up and simplifying improvements and updates.
- Interoperability: The uniform compatibility of various suppliers' software programs and hardware components is made possible via standardised interfaces between layers. In circumstances with heterogeneous networks, interoperability is critical.
- Troubleshooting and Debugging:
Layered architecture makes it possible to isolate issues into particular layers, making finding and fixing community issues simpler.
- Scalability: As networks develop in size and complexity, extra layers or protocols may be delivered to accommodate new requirements without disrupting existing functionalities.
- Security: The layered technique allows security features to be applied at a couple of degrees, protecting the community from various threats.
- Efficiency: Each layer specialises in a selected factor of verbal exchange, optimising aid allocation and performance.
Evolution of Layered Architecture
The idea of layered architecture in laptop networks can be traced back to the 1960s when the need for standardisation and interoperability in networking became obvious. Over time, several fashions and protocols have emerged, with the OSI version and the TCP/IP suite being the most influential.
1. OSI Model
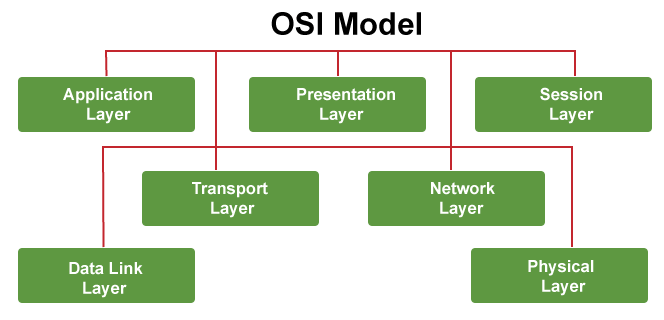
Proposed utilizing the International Organization for Standardization (ISO) in the late 1970s, the OSI model provided a conceptual framework for networking. Though it didn't take advantage of big adoption as a realistic model, it substantially influenced network design ideas.
2. TCP/IP Suite:
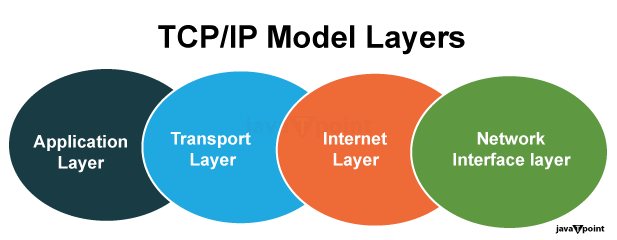
In comparison, the TCP/IP suite, developed by the U.S. Department of Defence in the Nineteen Seventies, has become the foundation of the present day's Internet. It condensed the OSI model into 4 layers: Network Interface, Internet, Transport, and Application. TCP/IP's fulfilment may be attributed to its simplicity and flexibility.
Layered Architecture Components and Functions
- Physical Layer: At the bottom of the OSI model, the Physical Layer offers the actual hardware components and physical transmission of facts. It encompasses aspects including cable sorts, connectors, signalling, and the modulation of alerts. Ethernet cables, fibre optics, and Wi-Fi indicators all fall underneath this residue.
- Data Link Layer: Above the Physical Layer, the Data Link Layer specialises in setting up a reliable hyperlink between two immediately linked nodes. It regularly employs MAC addresses for device identification and consists of mistake detection and correction mechanisms. Ethernet and Wi-Fi protocols operate at this residue.
- Network Layer: The Network Layer is liable for routing facts among networks. It manages logical addressing (along with IP addresses), determines the most excellent path for information packets, and handles the routing of packets through routers. IP (Internet Protocol) is a distinguished Network Layer protocol.
- Transport Layer: Above the Network Layer, the Transport Layer guarantees reliable facts transfer between two hosts. It gives offerings including segmentation of facts, error detection, and go-with-the-flow management. TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are key Transport Layer protocols.
- Session Layer: The Session Layer offers consultation control among packages. It establishes, keeps, and terminates classes, ensuring that statistics trade among packages is coordinated and reliable. This layer is much less common in modern networking but became extra relevant in earlier networking models.
- Presentation Layer: Situated above the Session Layer, the Presentation Layer focuses on facts translation and encryption. It ensures that records exchanged among extraordinary systems are in a layout they can understand. Encryption and decryption, information compression, and character encoding are a part of this layer's functions.
Application Layer: The topmost layer, the Application Layer, interfaces with end-consumer programs without delay. It presents many network offerings and protocols, such as HTTP for net surfing, SMTP for e-mail, and FTP for file transfer. It's the layer in which users interact with the community.
Benefits of Layered Architecture
- Simplified Design and Development: By breaking down network functionality into discrete layers, the layout and development of networking technologies turn out to be extra doable and less complicated.
- Interoperability: The standardised interfaces among layers facilitate interoperability between one-of-a-kind networking devices and technology. This method allows gadgets from diverse manufacturers to work collectively and seamlessly.
- Ease of Maintenance: Troubleshooting and preservation become more sincere, while problems can be remoted to precise layers. This hastens the detection and resolution of problems in the network.
- Scalability: Layered structure allows for adding recent layers or protocols to deal with evolving community requirements, making networks more adaptable to converting desires.
Real-World Applications and Examples
Layered structure is an essential concept in modern-day networking, and it finds utility in diverse real-world situations.
- Web Browsing: When you open a web browser and visit an internet site, the Application Layer handles the interplay with the browser. It requests net pages (HTTP) transmitted over the community through the lower layers. The facts are segmented and reassembled on the Transport Layer, routed on the Network Layer, and transmitted over the bodily medium on the Physical Layer.
- E-mail Communication: Sending an e-mail entail multiple layers. The Application Layer interfaces with your e-mail patron (e.g., Outlook or Gmail). The e-mail is formatted and encrypted at the Presentation Layer, segmented on the Transport Layer (SMTP), routed on the Network Layer, and delivered through the Data Link Layer for your electronic mail server for eventual transmission.
- VoIP Calls: Voice over Internet Protocol (VoIP) calls use the Application Layer for call initiation and management. The voice information is encoded and compressed on the Presentation Layer, segmented on the Transport Layer (using protocols like RTP), and transmitted over the network layers to reach the recipient. VoIP offerings like Skype and Zoom depend upon layered architectures to ensure the dependable and real-time transmission of voice and video information over the Internet.
- Cloud Computing: Cloud offerings depend heavily on layered architectures to ensure statistics integrity, safety, and efficient aid management. Where cloud services are hosted, data facilities hire complicated networks with layered architectures to supply offerings to end-users.
- Internet of Things (IoT): IoT devices, together with clever thermostats, sensors, and cameras, speak with cloud offerings via layered network architectures. These architectures ensure data is transmitted reliably and securely among gadgets and cloud servers. The IoT ecosystem, comprising diverse, interconnected gadgets, is based on layered architectures to ensure green conversation and data change among gadgets and cloud offerings.
- Internet Protocol Suite (TCP/IP): The Internet relies closely on the layered structure of the TCP/IP suite. This suite has been instrumental in the boom and achievement of the worldwide community.
- Wireless Communication: Wireless networks, such as Wi-Fi and mobile networks, use layered architectures for efficient data transmission and reception. FOR EXAMPLE, the IEEE 802. Eleven standards for Wi-Fi carry a layered method.
- Ethernet: Ethernet, a broadly used stressed networking generation, employs a layered architecture that adheres to the OSI version. This enables Ethernet devices from one-of-a-kind manufacturers to work collectively seamlessly.
- Data Centres: Large-scale records centres that power cloud computing services use layered architectures to control information glide and hold high availability.
- Video Streaming: The layered architecture guarantees easy playback when you circulate a video on platforms like Netflix or YouTube. The video statistics are split into packets on the Transport Layer, routed through networks at the Network Layer, and added in your tool wherein it's reassembled and displayed via the Application Layer (e.g., video player).
- Blockchain Networks: A form of layered architecture exists even in blockchain networks like Bitcoin and Ethereum, which can be decentralised and depend upon a peer-to-peer network. The lower layers manipulate the transmission of transactions and blocks via the network, even as the higher layers contain the software common sense for executing smart contracts and interacting with the blockchain.
Challenges and Future Trends
While layered architecture has been especially a hit, it additionally faces demanding situations and ongoing developments:
- Security: Network protection is an ongoing undertaking, and each layer of the structure should be secured in opposition to threats like hacking, records breaches, and malware. Future tendencies in network safety may additionally contain AI-driven threat detection and advanced encryption techniques.
- 5G and Beyond: The advent of 5G networks introduces new demanding situations and possibilities for layered architectures, mainly in managing large fact volumes, low-latency communication, and supporting a variety of gadgets.
- Edge Computing: Edge computing, which entails processing facts closer to the source of the record (as opposed to in centralised statistics centres), is reshaping layered architectures. Edge networks must be designed to manipulate facts efficaciously flow from facet gadgets to the cloud and back.
- Automation and Orchestration: Network automation and orchestration are becoming increasingly crucial for coping with complex networks successfully. These developments involve software-defined networking (SDN) and community function virtualisation (NFV) to automate community provisioning, configuration, and maintenance.
- Complexity: As networks evolve and comprise new technologies, managing the complexities of layered architectures becomes more difficult. Network administrators must stabilise performance, security, and scalability.
- Convergence: The boundary between layers is becoming much less wonderful as cutting-edge networks demand more flexibility. Converged protocols and technologies are rising to cope with this problem.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are increasingly used to optimise community control and safety. AI-driven analytics can discover network anomalies, automate network configuration, and enhance security by identifying and responding to threats in real-time.
- Containerisation and Microservices: Adopting containerisation technology (e.g., Docker) and microservices architectures is converting how packages are deployed and managed. These trends affect the Application Layer, allowing more bendy and scalable utility development and deployment.
- Quantum Networking: Quantum networking, a burgeoning discipline, can disrupt conventional networking paradigms. Quantum communique protocols, such as quantum key distribution (QKD), introduce new protection and encryption mechanisms that could require changes to current layered architectures.
- Network Slicing: In 5G networks, community cutting is being explored. Network reducing permits operators to create digital network instances within a physical community infrastructure, each tailored to specific use instances. This generation requires progressive strategies for community architecture to ensure efficient resource allocation and isolation between slices.
Conclusion
The OSI version and the TCP/IP suite constitute exquisite examples of how layered architecture in computer networks has been critical in forming the modern digital age. It has become an important element of community layout because of its modularity, compatibility, and scalability. The layered architecture will exchange with technology, ensuring networks live robustly, effectively, and stable in the face of clean possibilities and dangers.
|



 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now










