What Is the Dark Web and Should You Access It?What exactly is the Dark Web?The dark web refers to the web section where information has been encrypted and is inaccessible to traditional search engines. Accessing the dark web necessitates using specific browsers, such as Tor Browser. Using the dark web, as opposed to regular websites, provides a high level of privacy and anonymity. 
As a result, the dark web is most commonly associated with online drug markets, trades for stolen data, and other illegal activities. Despite this, people who use the dark web for real purposes, such as political dissidents or those who wish to keep specific information hidden, are also common. The dark web is also referred to as the darknet or black web. In-Depth Understanding of the Dark WebAs the name indicates, the dark web is a hidden underground network. It comprises a collection of websites that are closed to the general public. This implies they can only be found using some techniques other than regular search engines like Google or Bing. Because traditional search engines have the tendency to index links from public websites, they produce results from those websites accordingly. These results are sorted by keywords and relevance. On the other hand, the dark web uses information that isn't available or accessible to traditional search engines, such as content from private accounts like email, social networking, and banking, as well as personal and professional databases and documents. There is a lot of unprofessional content on the dark web. It is regularly linked to illicit and criminal conduct. IT titans and giant media conglomerates somewhat hold virtually some power over the dark web. It also gives legal authorities extra powers to capture those who engage in immoral behavior. The dark web first appeared in the early 2000s, concurrently with the development of Ian Clarke's Freenet, which was intended to protect users from government intervention and cyber attacks. The system, still in use today, allows users to express themselves freely online without fear of being tracked. Later, the project named Onion Router was funded by the US Naval Research Laboratory. With Tor (a web browser) aiding in the project, it was made possible for intelligence sources to communicate easily and securely, particularly in hostile environments where personal safety was critical. Due to this, Tor has quickly become one of the most popular dark web browsers. It uses databases to assist users in navigating and locating the information they require. With the rise of cryptocurrencies, the dark web has become even more popular, particularly among cybercriminals. This is because the exchange of digital currencies on the dark web often helps buyers and sellers to remain in high anonymity. Because of its association with certain illegal activities, the dark web has been called for regulation many times. For example, the G20 and the Financial Action Task Force (FATF) have urged cryptocurrency companies to provide information on buyers and sellers in online transactions. This is especially important, as they claim, in assisting law enforcement in tracking down criminal organizations and illicit activities. Why do people use the 'Dark Web'?People may use the 'Dark Web' for various reasons; however, three main reasons include the following: Illegal ActsThe Dark Web may be used by people who want to engage in illegal online activities such as selling weapons or drugs. These types of operations and the websites that provide them are often categorized as Hidden Services. IdentificationPeople may wish to safeguard their online identity for several reasons. In some cases, this is due to the risk of their identity being revealed, such as in countries where the government prohibits free press or political censorship exists. Others may use it to reduce their chances of becoming a victim of crime, such as those who have been cyberstalked or are concerned about online banking security. Tor is primarily used to browse the open web anonymously; however, hidden services account for a very small portion of its traffic. Obtaining 'Hidden Services'It includes services in which Tor protects both the user's anonymity and the website's anonymity. The site's IP address cannot be determined, which obscures information about its host, location, or content. Hidden Services are sometimes called "onion addresses" because their URLs frequently end in .onion. Tor is not a Hidden Service in and of itself, but the sites it hosts are. Hidden Services can be used for legitimate purposes like whistleblowing or allowing members of the public to share sensitive information like criminal knowledge without fear of retaliation. Although, it is widely assumed that most Hidden Services contain illegal content. They frequently necessitate registration (username, password, etc.). Some have 'VIP' sections that can only be accessed with an administrator's invitation or via a member-created and approved application. What is the distinction between the 'Open Web', 'Deep Web', and 'Dark Web'?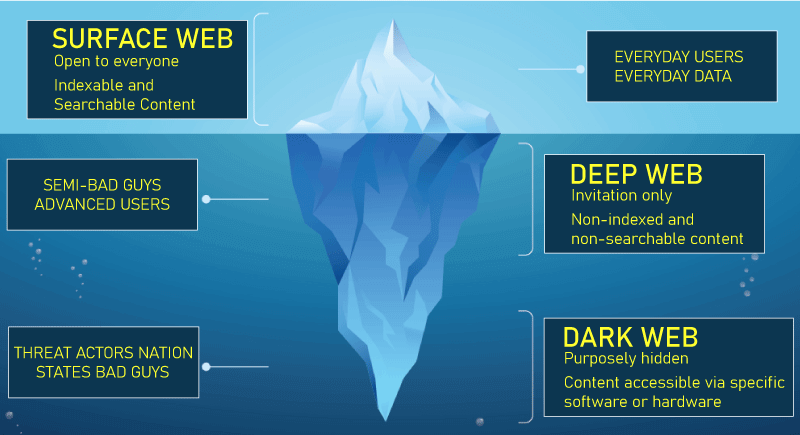
Open WebThis is the most visible part of the internet and can be accessed via search engines like Google or Bing. The open web is also sometimes referred to as the 'Surface Web'. The Deep WebThis section of the internet is usually off-limits to the general public. It cannot be found using traditional search engines or other less well-known methods. Most of the 'Deep Web' is made up of databases that can be accessed securely via the 'Open Web'. For example, databases associated with hotel reservations, online purchases, medical records, banking, and other activities. The content is password-protected, and only authorized users, such as employees, clients, or customers, can access it. The Dark WebMost people connect to the internet using a computer or device with an IP (Internet Protocol) address, which serves as their online identity. An IP address allows networks to send data to the proper location, such as ensuring that an email is delivered to the intended recipient. An IP address can track and monitor a person's internet usage. The 'Dark Web' employs sophisticated systems to mask a user's true IP address, making it difficult to determine which websites a device has visited. It is usually accessed through specialized software, the most well-known of which is Tor (The Onion Router). Tor is used by approximately 2.5 million people every day. Tor is not the 'Dark Web' but rather a way to navigate both the Open and Dark Webs without being identified or tracked. How does one gain safe access to the dark web?These are the steps to take to access dark web resources: Consider Buying a VPNA VPN will mask the location and prevent online breadcrumbs from leading back to the individual, securing the real identity like location or IP address. While a VPN is active, all connections are encrypted, preventing eavesdropping and Man-in-the-Middle (MITM) attacks. One can also choose from which location he wants to reveal his device's IP, and the VPN will use a network of servers and relays to mask his IP address, making his real IP address difficult to trace. VPNs can also be used to unblock geo-restricted streaming content. Many free options will either throttle the speed or collect the data, so the best options are paid-for and subscription-based VPN services. Set up the Tor BrowserTor browser prevents online fingerprinting, bypasses website blocks, and prevents trackers from creating profiles based on browsing habits. The Tor Browser employs multiple layers of encryption to enhance your anonymity. It has also integrated the DuckDuckGo search engine, which does not even save or log the search queries. Users may investigate the options, and if there is a need for a more secure experience, they select "safer" or "safest" criteria through preferences, which also disable potentially dangerous website functionality, such as rogue JavaScript. Thousands of volunteers worldwide operate the proxy servers that protect the identity on the Tor network. Tor Browser can be downloaded for Windows, macOS, Linux, and Android. For the best protection, it is recommended to use a VPN in conjunction with the Tor browser and connect to Tor via a VPN to add an extra layer of security. One may also consider using a virtual machine if one is concerned about malware or exploits (VM). Identify the OnionTo access a dark web resource, individuals must know its exact web address. Such websites often use top-level domain names that usually end with .onion, many of which are extremely long, random combinations of letters and numbers. Several directories host .onion links and websites but proceed with caution at all times. Some will take users to commercial sites, such as cryptocurrency mixers, drugs, and fake passports. Others, on the other hand, are not-for-profit platforms and offer legal content such as education and training workshops, forums, and personal blogs. What are the threats found on the dark web?
The following are some common threats you may encounter while browsing through the dark web: Malware SoftwareMalicious software, or malware, is alive and well-served on the dark web. It is generally offered in such portals to provide cyberattack tools to launch threats on users' devices. These potentially dangerous software always persist on the dark web, infecting unsuspecting users as it does elsewhere on the internet. Websites providers, however, use many social contracts to protect users on the rest of the internet that do not exist on the dark web. As a result, while browsing through the dark web, users may be regularly exposed to malware, such as:
If someone explores any dark web sites, they risk being singled out and targeted for hacks and other crimes. Most malware infections are detectable by endpoint security software. With Tor and the dark web framework, anonymity is powerful, but it could be better. Any online activity can leave breadcrumbs leading to the identity if someone digs deep enough. If someone's computer or network connection is compromised, the dangers of online browsing can spread into one's regular life. Government MonitoringLike many Tor-based sites being taken over by law enforcement agencies worldwide, there is a clear risk of becoming a government target simply for visiting a dark website. In the past, illegal drug marketplaces such as the 'Silk Roads' have been used for police surveillance. Using custom software to infiltrate and analyze activity, law enforcement has discovered the user identities of patrons and bystanders. Even if someone never buys anything, they may be watched and indicted later in life for other activities. Filtrations may subject anybody to surveillance for other types of activity. In some countries, it is a punishable offense to circumvent government restrictions to investigate new political ideologies. As a result, China uses the "Great Firewall" to block access to such websites. Visits to such content may result in placement on a watchlist or immediate incarceration. ScamsSome alleged services, such as professional "hitmen", may simply be scams designed to exploit unsuspecting customers. According to reports, the dark web provides various illegal services, ranging from paid assassinations to sex and weapon trafficking. Some of these are well-known and well-established threats that circulate on the internet. Others may take advantage of the reputation of the dark web to defraud users of large sums of money. Additionally, some dark web users may try to steal your identity or personal information in order to sell it and make money off others in return. Is it illegal to use and visit sites on the dark web?It is illegal only when the person does illegal activity against the law of the governing body to which he belongs. On the network side, the dark web is ambiguous. The use of the dark web typically indicates that someone is attempting to engage in an activity that one would be prohibited from doing in public. Government critics and outspoken advocates may fear repercussions if their true identities are revealed. People who have been harmed by others do not want their identity or information to be known to the attackers. However, anonymity has a disadvantage in that criminals, and malicious hackers prefer to operate in the shadows as well. Cyberattacks and human trafficking, for example, are activities that the participants may be committing crimes well aware of. Therefore, they take their actions to the dark web to conceal themselves securely. Since these activities fall under the category of illegal activity, those involved will be punished as per the law if caught. Additionally, browsing these areas is somewhat legal, but it may cause problems as well. While not illegal in and of itself, unsavory activity does exist in many parts of the dark web. People need to be more cautious considering the many types of threats on the dark web, such as advanced, computer-savvy users who are aware of its dangers. Otherwise, individuals may be exposed to unnecessary risks. The Bottom LineThe dark web is a relatively new concept in the history of the internet. Individuals can use it to remain anonymous while freely expressing themselves without fear of repercussions. However, this level of privacy has contributed to its negative reputation as a forum for those looking to engage in illegal activities. Suppose individuals want to use the dark web. It's as simple as installing a private browser, connecting to a VPN, and keeping someone's computer safe and secure.
Next TopicAbsolute Value
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









