Access Ports Vs Trunk PortsIn the realm of computer networking, the terms "access" and "trunk" carry substantial weight, delineating crucial functionalities within the intricate web of interconnected devices. In essence, an "access" port serves as the gateway for end devices to connect to the network. This pivotal point allows computers, printers, and other peripherals to communicate and share information within a specific local area network (LAN). Access ports are closely associated with Virtual Local Area Networks (VLANs), which act as digital partitions in a network. These VLANs help organize and secure the network by creating distinct segments based on specific criteria. By employing access ports and VLANs, networks can achieve both efficient organization and heightened security as devices communicate within designated and restricted segments. On the other hand, a "trunk" port operates on a broader scale, acting as a conduit for the transmission of data between switches and other network devices. Unlike access ports, trunk ports possess the capability to transmit multiple VLANs simultaneously, making them indispensable in scenarios where complex networks demand seamless communication across various segments. The significance of access and trunk ports lies in their role as the building blocks of a well-structured and efficiently functioning network, shaping the flow of information and ensuring the cohesion of diverse devices within the digital landscape. 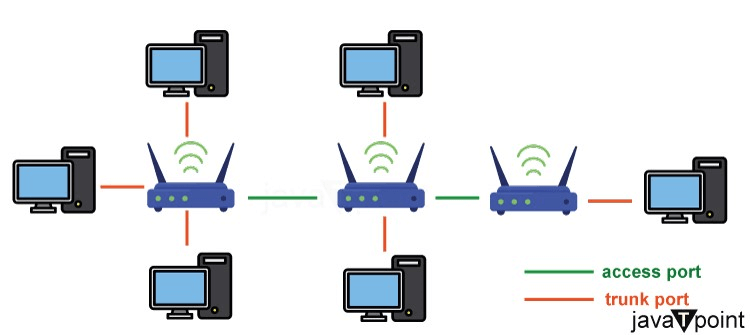
Access PortsAccess ports function as the pivotal entry points connecting our regular gadgets think computers and printers to the expansive network. At their core, these ports serve a crucial purpose: they empower our devices to interact effortlessly, not only with each other but also within the larger network. It's like they create a smooth pathway, allowing data to flow seamlessly within a specific local area network (LAN). In simpler terms, access ports are like traffic controllers, ensuring that communication between our devices and the broader network happens without any hitches. Now, what makes access ports particularly interesting is their connection to Virtual Local Area Networks or VLANs. These are like virtual partitions within the network, organized based on certain criteria. Access ports play a vital role in configuring these VLANs, offering a way to divide the network for better organization and security logically. Imagine a company where different departments need their isolated communication access ports, with the help of VLANs, make this possible. The application of access ports spans various scenarios and industries. In schools, they're set up in classrooms, linking computers and devices to the school network. In healthcare, access ports ensure that medical equipment and computers can seamlessly share crucial patient data. Even in hotels, you'll find access ports in guest rooms, providing connectivity for personal devices. Think about it in a manufacturing plant access ports are the connectors for machinery and control systems, allowing real-time data exchange for efficient production processes. The adaptability of access ports makes them essential in numerous contexts, serving as the vital link connecting our devices to the broader network. In essence, access ports act as the gatekeepers, ensuring a smooth flow of information between our devices and the intricate web of the network infrastructure. Trunk PortsTrunk ports serve as the critical backbone of networking architecture, playing a key role in linking switches and other network devices. Their immediate purpose is to ensure the smooth transmission of data among these devices, thereby enabling effective communication throughout the entire network. In essence, these ports act as essential conduits, facilitating the seamless flow of information and contributing to the overall efficiency of the network. One of the distinguishing features of trunk ports is their ability to transmit data for multiple Virtual Local Area Networks (VLANs) simultaneously. Unlike access ports, which are more localized in their scope, trunk ports can carry information from various VLANs, making them essential in scenarios where network segmentation is critical. This capability ensures that data from different VLANs can travel through the same physical connection without becoming intertwined, maintaining the integrity and organization of the network. To achieve this, trunk ports employ trunking protocols, with IEEE 802.1Q being one of the most widely used standards. This protocol adds a VLAN tag to the Ethernet frames, providing a way to differentiate and segregate traffic from different VLANs as it traverses the trunk. By tagging the frames, trunking protocols enable switches at both ends of the trunk to understand and properly direct the data to its intended VLAN. This ensures that even though multiple VLANs share the same physical connection, their data remains distinct and identifiable. Trunk ports find extensive use in various scenarios where network complexity and the need for efficient data transmission are paramount. In enterprise environments, especially those with large and diverse departments, trunk ports are deployed to connect switches on different floors or across buildings. This enables the seamless flow of information between various segments of the organization without compromising security or efficiency. In data centres, trunk ports are indispensable for connecting servers to the network. Given the diverse applications and functions of servers within a data centre, trunk ports ensure that data from different VLANs can be transmitted to and from servers without bottlenecks or data congestion. Overall, trunk ports serve as the conduits for interconnecting different segments of a network, allowing for the efficient and secure flow of data in scenarios ranging from large enterprises to complex data centre environments. Their ability to handle multiple VLANs and employ trunking protocols makes them instrumental in maintaining well-organized and high-performance network architecture. Differences between Access and Trunk Ports
Understanding the differences between access and trunk ports is vital for effective network management. Access ports cater to the communication needs of individual VLANs, providing a straightforward and secure approach. Trunk ports while more versatile, demand careful configuration to prevent security vulnerabilities and maintain efficient data flow across diverse VLANs. Misconfigurations in either type of port can compromise network performance, emphasizing the importance of accurate configuration for optimal functionality and security. Best Practices for Configuring Access and Trunk PortsConfiguring Access and trunk ports effectively is crucial for maintaining a secure and well-performing network. Here are best practices for each, along with essential security considerations: Configuring Access Ports
Configuring Trunk Ports
Security Considerations for Both Access and Trunk Ports
Real-World ApplicationsIn retail environments, the choice between access and trunk ports is pivotal for Point of Sale (POS) systems. Access ports are employed at individual checkout terminals, ensuring secure communication between the cashier's device and the main sales network. Trunk ports come into play at the network switch level, facilitating the transmission of transaction data between different VLANs, such as sales and inventory. Similarly, in educational institutions, access ports are strategically utilized in classrooms to connect computers and other devices to the school's network. On the administrative side, trunk ports are essential for managing various VLANs, like student and faculty networks, optimizing communication, and maintaining security protocols. Impact of Network Growth and ScalabilityAs networks expand to accommodate growing numbers of devices and users, the scalability of port selection becomes paramount. Access ports, while efficient for localized connections, may need to be improved in handling the increased demand for individual connections. Trunk ports, with their ability to manage multiple VLANs and diverse traffic, have become increasingly valuable in scaling up network infrastructure. Moreover, in scenarios where network growth involves the addition of new departments or services, trunk ports offer a more flexible and scalable solution. Their capacity to handle the complexity of expanded VLANs ensures that the network remains agile, adapting to the evolving demands of a growing organization. Ultimately, the choice between access and trunk ports plays a vital part in shaping the efficiency and adaptability of a network as it evolves. Case StudiesCase Study 1: Retail Network Optimization In a retail setting, the implementation of access and trunk ports played a pivotal role in enhancing network efficiency. Access ports were strategically deployed at individual cash registers, ensuring secure communication for sales transactions. Meanwhile, trunk ports were employed at the switch level, seamlessly transmitting data between sales and inventory VLANs. This choice facilitated a streamlined point-of-sale experience while maintaining a robust inventory management system. Case Study 2: Academic Network Segmentation An educational institution faced connectivity challenges in classrooms and administrative offices. The introduction of access ports in classrooms improved local communication by connecting computers to the school's network. Simultaneously, trunk ports were instrumental in managing distinct VLANs for student and faculty networks, ensuring efficient communication and adhering to security protocols. This balanced approach significantly enhanced network functionality and adaptability across diverse academic environments. ConclusionIn conclusion, this exploration of access and trunk ports underscores their indispensable roles in the intricate tapestry of network architecture. Access ports act as gateways, connecting end devices seamlessly within specific VLANs promoting localized communication. On the other hand, trunk ports, the backbone of inter-device connectivity, efficiently transmit data across multiple VLANs, fostering network-wide cohesion. Understanding the nuances between access and trunk ports is paramount for effective network management. The delineation of these ports, their best practices, and real-world applications illuminate their significance. Whether configuring for retail transactions, educational institutions, or diverse industries, the careful choice of port types proves pivotal. As networks evolve, the scalability considerations and security implications associated with these ports become even more critical. Therefore, network administrators must grasp these distinctions to optimize functionality, security, and adaptability, ensuring the seamless operation of networks in the dynamic digital landscape.
Next TopicEdge Routers
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









