Authentication ServerWhat is an Authentication Server?A program that helps an individual trying to access a network authenticate itself is called an authentication server. Such an entity could be another server or a human user. An authentication server can be housed in a network accessible server, an Ethernet switch, an access point, or an independent machine. 
Various kinds of Servers for AuthenticationMultiple web servers are available for authentication. A variety of devices and techniques are used in multiple authentication systems, such as encrypted sockets layer, transport-layer security, Active Directory, Lightweight Directory Access Protocol, and Remote Authentication Dial-In User Service (RADIUS). RADIUS is among the majority of frequently utilized authentication methods. With Unix networks, Terminal Access Controller Access Control System Plus (TACACS+) is used in a manner equivalent to RADIUS. TCP is utilized by TACACS+, while User Datagram Protocol is used by RADIUS. Various kinds of protocols for authenticatingDetermining if someone or something is who or what it claims to be is the process of end-user authentication, which allows users to access user accounts. Although there are various kinds of authentication, we'll only discuss the two most common ones here: single-factor and multi-factor authentication. The two primary types of authentication are multifactor authentication (MFA) and single-factor authentication. 
1. Single-factor authentication: It's possible that a username and password are the sole pieces of identification needed when a prospective subscriber visits an authentication server. After the user's identity has been confirmed, the authentication process is finished. 2. Multifactor authentication: In addition to inputting the login information, an individual must perform a further process to be able to get access, such as providing a password that is unique to them or clearing a CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart). To access a certain service, for instance, a subscriber using Kerberos must request and obtain an encrypted security token. Many customized authentication servers combine electronic cards, Internet Protocol (IP) addresses, or fingerprints with a number of the aforementioned methods. Operations of an Authentication Server in the WorkdayIn a nutshell, authentication is the process of verifying the identity of a computer or person via identification. To confirm this, a device or program may request multiple unique identifiers. Typically, each identifier belongs to one of these three groups:
What is Not Performed by an Authentication Server?Although an authentication server performs a lot of work in the background, it's critical to know what functions it does not perform. Authorization vs AuthenticationUp until now, the examples have involved the authentication server confirming a user's identity and providing the information back to the application that requested it. The application will decide what happens next. 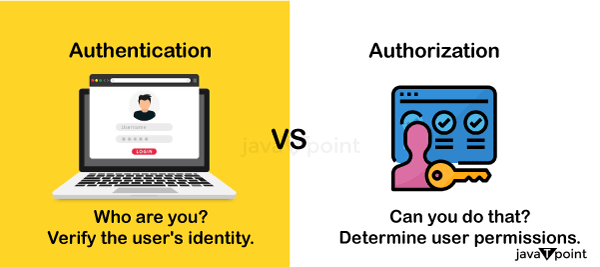
Authority: The application typically has to choose what the user can access once it has determined who they are. We call this authority. Authorization: Authorization is the process of confirming the resources that a user is authorized to access. Identification confirmation is the process known as authentication. Although it's simple to mix up authorization with authentication, it's critical to know the differences. The technique of authenticating has no bearing on what an individual may access.
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









