Ring Topology in a Computer Network
What is a Network?
A network is the combination of a set of devices that are connected by links. We can connect computers, phones, and other devices through the network. We can also connect the network wired or wirelessly.
What is Topology?
The study of shape and figure is known as tolopoly in computer networks. In topology, we can study the transmission of shapes and figures. That means we can have a shape; we can stretch it, turn it, or even bend it, and topology will tell us how to do that without tearing it or breaking it.
There are mainly two types of topologies available in the computer network. One is point-set topology, and the other is algebraic topology.
- Point-set topology:
Point-set topologies are also known as general topologies or set-theoretic topologies. It is a branch of mathematics that focuses on studying topological spaces. Topological spaces are abstract mathematical structures used to capture the notion of continuity, convergence, and other fundamental properties of spaces without relying on concepts like distance or metric.
- Algebraic topology:
Algebraic topology is a branch of mathematics that combines algebraic and topological techniques to study topological spaces and their properties. The main focus is associating algebraic structures (such as groups, rings, and modules) to topological spaces to capture essential topological information. This allows mathematicians to study topological spaces through algebraic methods, making complex topological problems more accessible.
In computer science, the term "topology" is being used in a different context than its use in mathematics (point-set topology or algebraic topology). In computer science and computer networks, topology refers to the arrangement or layout of the connections or links between network devices (such as computers, routers, and switches) in a network. Network topology defines how these devices are interconnected and how data flows between them.
There are various types of topologies available in the computer network. Ring topology is one of them. In this article, we are going to learn about the ring topology.
What is a Ring Topology?
Ring topology is a type of network configuration in which devices (such as computers or network switches) are connected in a circular or ring-like manner. Each device in the ring topology is connected to exactly two neighbouring devices, forming a closed loop. Data travels around the ring in a unidirectional or bidirectional manner, and a token-passing mechanism is often used to control data transmission. Ring topologies are known for their reliability and built-in fault tolerance, as data can still circulate in the opposite direction if part of the ring is disrupted.
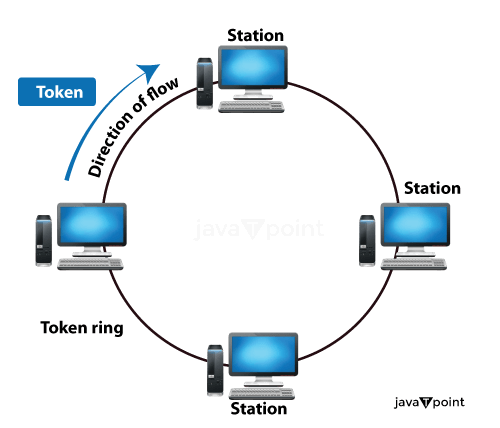
Ring topology is a network setup often used in local area networks (LANs) and wide area networks (WANs). In this setup, computers are connected circularly using either RJ-45 network cables or coaxial cables, depending on the network cards in use. What's unique about a ring topology is that it doesn't require a central hub to work. Setting up and fixing issues with this type of network is generally straightforward compared to other configurations.
However, there's a potential drawback: if one computer in the ring fails to transmit data, it can disrupt the entire network. To address this issue, some ring setups use a dual-ring structure. Information is transmitted clockwise and counter-clockwise, providing a backup route if one direction fails. These more robust systems are called redundant ring structures and enhance network reliability.
How does Ring Topology Work?
The ring topology is a network configuration in which all the devices are connected in a circular or ring-like structure. The data can be transmitted from one device to another in the ring topology until it reaches the destination. The total ring topology works based on the below process.
- Physical Connection:
In this step, each device is connected to exactly two neighbouring devices. We can connect by means such as Ethernet cables, optical fibres, or wireless links depending on the technology used.
- Unidirectional or bidirectional:
The data can be transmitted in either unidirection or bidirection in the ring topology. In a unidirectional ring, data travels in only one direction around the ring. Data can travel both clockwise and counterclockwise in a bidirectional ring.
- Token Passing: In the ring topologies, the token passes the protocol, which is further used to manipulate data transmission. A token is a particular control packet or signal continuously circulating the ring. Only the device that is holding the token is allowed to transmit data onto the network.
- Data Transmission: When there is a need to transmit data between the devices, they must wait for the token to reach them. Once it receives the token, it can attach its data and send it to the ring. The data travels from device to device, and each device checks if it is meant for it. If it is, the device receives the data; otherwise, it simply passes it along.
- Data Reception: When the data completes its process around the ring, returns to the sender, or reaches its intended destination, the recipient extracts, and processes all the data. Other devices continue to pass the token until it is needed again.
- Reliability: Ring topologies are generally reliable because they have a closed-loop structure. If one segment of the ring is disturbed due to a cable break, then the data can still travel in the opposite direction, maintaining network connectivity. However, if a device fails or the token circulation mechanism faces problems, it can disrupt the entire network.
- Dual-Ring and Redundancy: Some ring networks use a dual-ring structure to address the potential issue of a single point of failure. Data is transmitted in both directions (clockwise and counterclockwise) simultaneously, providing redundancy. These systems are known as redundant ring structures and offer increased reliability.
- Scalability: we can scale the ring topologies by adding more devices. When the network grows larger, it may become more challenging to manage and maintain.
- Performance: Ring topologies will offer low latency, and their performance will be predictable because data travels directly from one device to the next without collisions, like bus topologies.
How is Ring Topology Formed?
We can create the ring topology by connecting all the devices in a circular or ring-like structure. With the help of the following things, we can make the ring topology.
- Physical Connections: All devices, like computers, servers, switches, or network nodes, are physically connected using network cables or communication links. These connections are point-to-point. The point-to-point means that each device is connected directly to two neighbouring devices.
- Cabling: We can use the cable based on the technology that we have used. Ethernet-based ring topologies commonly use twisted-pair Ethernet cables (RJ-45) or optical fibre cables for physical connections. Other technologies might use coaxial cables or wireless links.
- Configuration: all the devices are arranged in such a way that they form a closed-loop or circular structure. Each device connects to its two immediate neighbours in the ring. This configuration can be unidirectional (data flows in one direction around the ring) or bidirectional (data flows in both clockwise and counterclockwise directions).
- Token Passing (Optional): There are so many ring topologies in which the token passing protocol can manipulate the data transmission. In this case, a token (a special control signal or packet) circulates the ring. Only the device holding the token can transmit data onto the network. Token passing helps prevent data collisions.
- Initialization: we can start the connection by introducing the token into the network by one of the devices. This signal begins circulating the ring, and devices wait to access the network.
- Data Transmission: when there is a need for the transmission of data between devices, it must wait for the token to reach it. Once it has the token, it can attach its data and send it around the ring. The data travels from device to device, with each device checking if it is meant for it. If it is, the device receives the data; otherwise, it simply passes it along.
- Data Reception: When the data completes its journey around the ring, returns to the sender, or reaches its intended destination, the recipient extracts and processes the data.
- Continuous Operation: The token or data circulates the ring, and devices continue to access the network when they have the token.
- Reliability: Ring topologies are designed in such a manner that they should provide reliability. If a cable segment or a device fails, then the data can still travel in the opposite direction around the ring, ensuring network connectivity. However, if a device fails or issues with the token circulation mechanism, it can disrupt the network.
- Redundancy (Optional): Some ring networks implement redundancy using a dual-ring structure. Data is transmitted in both directions (clockwise and counterclockwise) simultaneously to enhance fault tolerance. These setups are known as redundant ring structures.
Applications of Ring Topology
Ring topology has applications in various contexts, particularly where reliability and predictable performance are important. Here are some common applications of ring topology:
- Local Area Networks (LANs): Ring topology has been previously used in LANs, where a small to medium-sized group of computers and devices need to be interconnected. Token Ring, an older LAN technology, employed the ring topology. While Ethernet has largely replaced token rings in LANs, ring topologies can still be found in specific legacy networks.
- Industrial Control Systems: Ring topologies are commonly used in industrial control systems and manufacturing environments. These networks require high reliability and low latency for process control and automation. Redundant ring topologies are frequently employed to ensure network availability.
- Fibre-Optic Networks: In fibre-optic communication networks, we use ring topology for data transmission between network nodes. Fibre-optic rings provide high bandwidth and can be configured with automatic protection switching (APS) to quickly reroute traffic in case of a fibre cut.
- Metropolitan Area Networks (MANs): Sometimes, we use ring topologies for metropolitan area networks that connect various locations within a city or region. Fibre-optic ring networks can provide high-speed connectivity for businesses, government agencies, and educational institutions.
- Telecommunications Networks: Telecommunications uses ring topologies in their long-haul and metropolitan networks to ensure fault tolerance. Synchronous Digital Hierarchy (SDH) and Synchronous Optical Networking (SONET) networks often employ ring topologies.
- Public Safety and Emergency Services: Ring topologies are also used in communications between public safety networks and emergency services. It also ensures constant connectivity and fault tolerance, critical in these applications, where communication can be a matter of life and death.
- Airport and Transportation Networks: Ring topologies are also used in airports, seaports, and transportation hubs to connect various systems, such as security cameras, passenger information displays, and baggage handling systems. Redundant rings ensure continuous operation.
- Smart Grids: Ring topologies are used to create redundant communication networks. In the context of smart grids for electrical power distribution, This helps monitor and control power distribution, detect faults, and manage electrical loads efficiently.
- Video Surveillance Systems: In large-scale video surveillance systems, where numerous cameras are spread across an area, ring topologies can ensure reliable data transmission back to a central monitoring station. Redundant rings help maintain surveillance even in the event of network failures.
- Mission-Critical Data Centers: Some data centres use ring topologies for internal network connectivity to ensure high availability and low-latency data access. Redundancy and fault tolerance are essential in data centre operations.
Advantages of Ring Topology
- Reliability:
Each device connected to the ring topology is fault-tolerant. If one link fails, the data flow does not stop, and the data reaches its destination. So, fault tolerance is the main advantage of the ring topology.
- Deterministic Data Flow:
In the ring topology, all the data travels predictably. This also has advantages for the ring topology. The main thing required for a topology is that the data should travel with consistent and predictable latency, such as in real-time communication or industrial control systems.
- Equal Access:
All devices connected to the ring topology have equal access to the ring topology network because it has no central server for data access. This method will protect the topology from network congestion or contention.
Disadvantages of Ring Topology
- Failure Impact: When ring topologies are resilient to single-point failures if the ring is broken at two points simultaneously (e.g., due to two device failures), the entire network can become disconnected. This situation is known as the "dual failure" problem.
- Limited Scalability: Expanding a ring network by adding more devices can be difficult and disruptive because it requires breaking the ring temporarily to insert the new device. This can be a significant drawback to growing networks.
- Cost: Ring topologies can be more expensive to set up compared to simpler topologies like bus or star. Each device must have two connections, which can increase cabling costs.
- Latency: Data packets must traverse the entire ring before reaching their destination. This can introduce some latency, especially in large networks with many devices.
- Complexity: It is very complex to manage and troubleshoot the ring topologies. Locating and repairing faults in the ring can be challenging, especially in larger networks.
|

 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now









