Initialization VectorWhat is an initialization vector (IV)?An initialization vector (IV) is an arbitrary integer that may be utilized in data encryption to thwart cyberattacks when combined with a secret key. It is a randomly generated integer, typically 128 bits in size, and is an integral part of symmetric key algorithms used for data encryption. This code, also known as a nonce (number used once), is utilized only once during each session in order to prevent a suspicious or malevolent actor from decrypting the data without authorization. 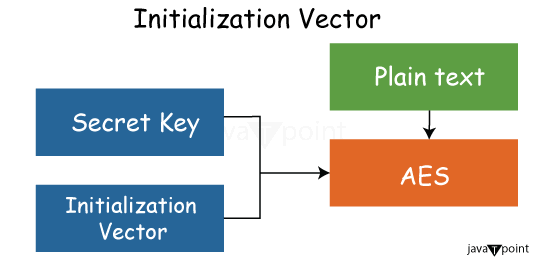
The significance of an initialization vectorWhen employing data encryption, an Initialization Vector (IV) plays a crucial role in preventing the repetition of ciphertext for identical plaintext sequences. In essence, the IV ensures that the encryption of the same plaintext sequence does not yield the same ciphertext sequence, thereby enhancing the security of the encrypted data. The primary purpose of an IV is to disrupt patterns that could be exploited by attackers. In the absence of an IV, if an identical plaintext sequence is encrypted multiple times, the resulting ciphertext would be the same. This repetition could provide attackers with hints to decode and interpret the original values, posing a risk of unauthorized access or hacking. By incorporating an arbitrary distinct nonce as the IV during encryption, recurrence becomes unnecessary, making it challenging for attackers to employ methods such as dictionary attacks. Since the encrypted data cannot be repeatedly read with the same IV, the likelihood of deciphering the communication is significantly reduced, bolstering the overall security of the encryption process. Characteristics of a perfect initialization vectorIV is used as an "initial state" in a cryptographic process. Encrypted data is hidden from hackers by the IV, making it more difficult for them to decipher it by trial and error or guessing. A random or pseudorandom number is the optimal IV. It has to be unique as well. To stop attackers from identifying patterns in identical sections of the encrypted communication and utilizing that knowledge to decipher the message, randomization and non-repetitiveness are essential. A hidden IV is not necessary. The destination computer often recognizes the IV, allowing it to decode the encrypted data upon reception. Therefore, both the donor and recipient must agree on the IV in advance. Additionally, IVs can be sent on their own or as part of session setup before any messages are exchanged. The encryption technique determines the IV length in terms of bits or bytes. The majority of the time, the length is equivalent to the length of the cipher's block or encryption key. Methods for granting the recipient access to the IVThe IV must be known by the receiver in order for them to decode the encrypted communication. To aid decryption, the IV may be made accessible to the receiver in a variety of ways. Sending it along in addition to the ciphertext is one method. Another method is to decide on the IV during the crucial handshake or conversation between the sender and the receiver. The IV may also be found by the receiver by monitoring certain factors, computing it progressively, or using the packet or cluster number, sender or recipient addresses, or any combination of these. Utilizing IVs in stream and block ciphersUsing a block cipher, we may concurrently encrypt data in blocks to create ciphertext. A stream cipher, on the other hand, encrypts and decrypts data one bit at a time. A symmetric key and algorithm are used by both stream and block ciphers to encrypt data. The two kinds of ciphers use distinct implementations of IVs. When using block ciphers in the Electronic Code Book (ECB) mode, which is a straightforward method of operation, the identical plaintext is always encrypted with the exact same key into the similar ciphertext. Otherwise, communication remains susceptible to compromise as the same plaintext encrypted with the same key results in the same ciphertext. This issue is resolved by appending an IV to the first block of the plaintext (XOR), which improves data security and integrity. An IV is added to the keyed internal secret state in stream ciphers. After that, before the first piece of output goes out, many cipher rounds are carried out. Stream ciphers are not completely secure even with the IV. Initialization vector in WEP IVA feature of the 802.11 standard that covers communications in wireless local area networks (LANs) is the Wired Equivalent Privacy, or WEP, algorithm. In order to encrypt data packets before transmission, WEP uses a secret key that is shared by a router and a mobile station. The stream cipher known as RC4 encryption is used by WEP. To make sure that packets are not altered while in transit, it carries out an integrity check. It makes use of a 24-bit IV for this. The message's cleartext portion contains the IV in the packet. Its objective is to prevent the encryption of two ciphertexts using the same key stream. Unfortunately, since the IV is brief, hackers may undertake statistical attacks to retrieve the plaintext and decrypt communications because the same key stream is often repeated. WEP is susceptible to a wide range of attacks, such as table-based attacks, where an attacker can quickly decode each packet using the same IV, passive attacks to decrypt traffic, and malicious data insertion. Active attacks for. Such vulnerabilities have made WEP encryption technology obsolete.
Next TopicWhat is Fiber Optics
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









