Extensible Authentication Protocol (EAP)As a protocol within wireless networks, EAP extends PPP (Point-to-Point Protocol) possibilities for authentication methods. Its main role in encrypted networks is to securely communicate identifying information for network authentication. From token cards, smart cards, and certificates to one-time passwords as well as public key encryption - EAP has it all. 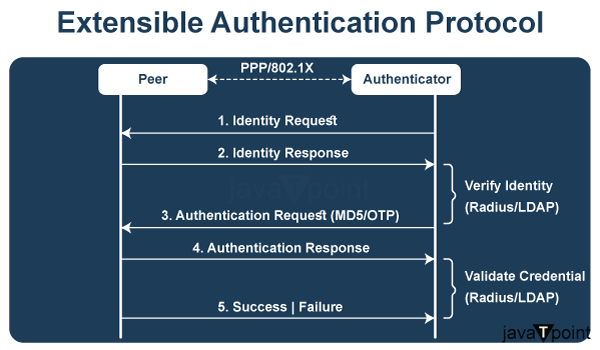
EAP methods aim to locate portals and ensure that only those with specific authentication keys or passwords may then use networks. Limiting users helps prevent network congestion and thus increases both the speed of networks and their security. In this way, organizations can adapt to the particular needs of privacy and internal company guidelines. The key characteristic of EAP is its modularity, providing a base around which extremely diverse authentication methods will function in tandem with future security requirements. Its simplicity can be matched to individual security requirements. EAP is implemented according to the 802.1x standard, playing an authenticating function within a local area network or wireless LAN (WLAN). This process involves three primary components: The user's wireless device, a WAP or authenticator as well as an authentication database/server. EAP types are chosen according to an organization or user's particular needs, and assure the passing on of authentication information between users and authenticator databases or servers. What is EAP's role in a wireless network?The Extensible Authentication Protocol (EAP) is a key piece in the machinery of wireless networks, giving PPP a license to use any authentication technique it desires. In encrypted networks, its main task is to securely transmit identifying information for network authentication. EAP's interoperability covers a spectrum of authentication methods, from token cards., smart cards, and certificates to one-time password and public key encryption. The basic feature of EAP is to strengthen portals, allowing networks to only users who have authentication keys or passwords. This method not only limits users but also protects against network congestion to increase speed and security. Its flexibility allows organizations to tailor the security solution directly to a specific level of privacy and target it accurately at internal company guidelines. EAP's most essential characteristic is extendibility, for in this manner, the various authentication methods can all operate smoothly on a common basis and respond to future security requirements. This simplicity can be tailored to fit specific security requirements and provides an operationally light yet secure infrastructure. EAP in Action: Understanding the Authentication ProcessPP operates per 802.1x standard protocol, functioning as the authentication technology in a local area network (LAN) or wireless LAN (WLAN). This intricate process involves three primary components: What EAP type is chosen depends on the specific requirements of an organization or user and permits authentication credentials to pass between the recipient (client) and source server. The authentication process through EAP unfolds systematically:
The authentication process uses EAP together with the Remote Authentication Dial-In User Service (RADIUS) protocol, and this way, messages can easily be passed back and forth between an authenticator server. EAP variants and their importanceEAP-MD5: EAP-MD5 was one of the earliest EAP methods. It provided only a basic level of authentication using the MD5 challenge-response mechanism. Yet its weakness to dictionary attacks and failure of mutual authentication meant that it was removed from most secure network environments. EAP-TLS (Transport Layer Security): By using digital certificates for both client and server authentication, EAP-TLS made major strides forward. It guaranteed strong two-way authentication and secure transfer of encrypted data between them. This version, which is based on SSL/TLS, became a standard building block for secure wireless networks and created a solid foundation to support subsequent EAP protocols. PEAP (Protected Extensible Authentication Protocol): PEAP is a response to the deficiencies in EAP-TLS, particularly cases where serious difficulties were encountered with client-side certificates. It added an outer authentication method by using TLS. In this way, the exchange of authentication credentials in a secure tunnel does not need client-side certificates and can be deployed more flexibly. EAP-TTLS (Tunneled Transport Layer Security): To overcome the weaknesses of both EAP-TLS and EAP-TLS, EAP required a two-stage authentication process. Like PEAP, it provides a secure tunnel but supports more varieties of inner authentication mechanisms. This flexibility makes it suitable for situations where differing authentication methods are needed. EAP-FAST (Flexible Authentication via Secure Tunneling): EAP-FAST was developed to deal with the difficulties involved in issuing certificates while maintaining security. It enables secure tunneling without the need for client-side certificates through mutual authentication using Protected Access Credentials (PAC) keys and so greatly improves efficiency while maintaining security. EAP-SIM (Subscriber Identity Module): First conceived for mobile networks, EAP-SIM uses SIM cards to verify users. So, it's no deal at all for a cell phone or PDA (personal digital assistant) to connect securely with any wireless network anywhere in the world. This approach exploits the security mechanism of the SIM, providing an effective means for authentication in cellular networks. EAP-AKA (Authentication and Key Agreement): Like EAP-SIM, another widely used technique in mobile networks is EAP-AKA. It employs the Authentication and Key Agreement protocol used in Universal Mobile Telecommunications System (UMTS) networks. EAP-AKA provides secure authentication and key agreement between mobile devices and the network. EAP-TLS 1.3 and EAP-TLS 1.2: Advances in the last few years have concentrated on strengthening cryptographic standards and security functions. Based on the most recent version of TLS, EAP-TLS 1.3 provides improved cryptographic algorithms and faster handshake protocols for greater overall security and efficiency. For newcomers to the Telecommunications sector in the 5G Era, EAP's security characteristic is native. In a 5G network, no matter which access network is used to connect to it, the authentication method works the same. This secure and adaptable function can be used on any kind of electronic equipment as long as there are intellectual property rights supporting it. EAP is an example. Modularity of EAP and future security trendsEAP, Extensible Authentication Protocol (EAP) is very important to secure communication in different environments of networking. Here are some potential trends and developments for EAP: Enhanced Security Measures: Robust security measures are likely to be added as EAP protocols take on new threats. This is going to involve tougher encryption, better authentication techniques, and resistance against attacks such as man-in-the-middle or brute force. Integration with Biometrics and IoT: As the role of biometrics in authentication gets larger and as more devices get connected to form the Internet of Things (IoT), there'll likely be developments in EAP, too. It could mean integrating EAP with biometric authentication or enhancing it to allow secure authentication within an IoT network. Compatibility and Interoperability: In the future, developments might center around making interoperability better between different EAP methods and devices. Some standards and protocols could be improved so that different systems can talk to each other more easily in a secure fashion using EAP, making it easier for there to finally be widespread adoption. EAP in Wireless Technologies: With the rapid development of wireless technologies like 5G, there will likely be some changes or improvements in EAP to meet the unique security needs of these networks. These are new challenges. Hopefully, EAP will evolve to meet this kind of high-speed and very large-capacity wireless communication requirement. Privacy Enhancements: With the rising focus on user privacy, future upgrades to EAP might include measures that would maximize and maintain a high level of security for authentication processes involving users, such as reducing exposure of personal data in actual accounting periods (including during various workshop handshakes). Post-Quantum Security: With the rise of quantum computing, one can imagine that as EAP itself advances, it may need to change over in order to be immune from a possible post-quantum age. Usability Improvements: Without compromising security, some effort to improve the user experience might be made to make EAP configuration and authentication easier for both end users and system administrators. Real-World Applications and Case StudiesCase Study 1: Corporate Network Security EnhancementScenario: A multinational corporation experienced difficulty in the security of its internal wireless network, coping with unauthorized intrusions and possible data losses. Solution: The company integrated certificate-based mutual authentication between network devices and users, depending on EAP-TLS for authorization. Each user's device was assigned a unique certificate through the use of EAP-TLS so that encrypted communication would be secure. Outcome: EAP-TLS greatly reduced the possibility of unauthorized access. Central management of certificates led to the development of a solid authentication process. The number of unauthorized access incidents fell precipitously, and this reduced the incidence of potential security vulnerabilities as well. Case Study 2: Educational Institution Network ProtectionScenario: Because so many users were connecting to the university's wireless network, maintaining a secure environment became almost an insurmountable problem. Network congestion and potential security holes threatened to hinder operations at any moment. Solution: The institution chose user authentication using server-side certificates, under which EAP-TTLS was adopted with Protected Extensible Authentication Protocol (PEAP) as an outer authentication method. This enabled the tunneling of authentication data securely, minimizing interception. Outcome: EAP-TTLS and PEAP fixed the network congestion problems. With centralized user authentication and encrypted exchange of this configuration information, the university has successfully secured its wireless network. Students and staff alike now enjoy a seamless but completely secure environment. Case Study 3: Healthcare Facility Data ProtectionScenario: This created a problem for one healthcare facility in securing patient data that was transmitted over its wireless network. The facility needed a solution that met strict regulatory standards without hindering its work. Solution: Using EAP-SIM for authentication, taking advantage of the standard Subscriber Identity Module (SIM) cards used in cellular devices, it also encrypted data transmission on a per-session basis using WEP keys. However, using EAP-SIM enabled secure authentication and data protection that is in accordance with healthcare regulations. Outcome: With EAP-SIM, secure data transmission was enabled while meeting healthcare regulations. This use of SIM-based authentication also increased the level of patient data protection, retaining confidentiality and integrity on a wireless network infrastructure. Case Study 4: Retail Chain Network Security EnhancementScenario: Unsecured wireless access points were proliferating in multiple store locations of a large retail chain. Customer data was at risk, and network vulnerability increased. Solution: The chain also used EAP-FAST for authentication and set up secure tunnels of mutual authentication between clients and servers. As EAP-FAST used a Protected Access Credentials (PAC) key for the provisioning exchange, secure authentication was possible without requiring server-side certificates. Outcome: EAP-FAST implementation greatly improved network security at stores. The retail chain hardened its wireless network by eliminating the need for server-side certificates in authentication, reducing possible weak points while still protecting customer information. These case studies illustrate how different EAP implementations deal with specific security challenges across various industries, reflecting well the efficiency of enhancing network security, maintaining compliance, and safeguarding sensitive data. The tailored EAP solutions provide an effective means to reduce security risks and protect the secrecy and integrity of wireless networks. EAP's Role and Native Security Features in Addressing 5G Challenges
While the 5G system encompasses a wide variety of access networks, EAP's strongpoint is its offering standardized and uniform authentication irrespective of network type. With this consistency, whether a device utilizes traditional cellular networks or next-generation IoT frameworks, the authentication process remains standardized across all devices to maintain uniform high levels of security throughout.
Flexibility is a fundamental feature of EAP, and this flexibility meets the different authentication needs in an extremely broad range of devices using 5G networks. From smartphones and tablets to IoT sensors, up through higher-grade autonomous vehicles that may be in contact with people's skin for long periods of time, EAP offers the flexibility needed to optimize authentication based on device type. This flexibility means that no matter which device connects to the network, it will be securely authenticated.
Methods such as EAP-TLS (Transport Layer Security) or EAP-TTLS (Tunneled Transport Layer Security), based on the Extensible Authentication Protocol, are used to ensure strong mutual authentication between a device and network access point. This is vital for 5G networks in particular. The authentication process produces mutual confidence and secure channels, strengthening data security. The mechanism of mutually authenticating each other means that EAP detects intrusive attempts to access its proprietary information and alerts the network, preventing outside interception.
While revolutionary, the advent of network slicing in 5G brings with it security concerns arising from this segmentation into multiple virtual networks based on a common infrastructure. Authentication is one of the most important aspects of EAP's role in securing network slices. Also, by using EAP-based authentication for each slice, access can be controlled. The fact that each slice authenticates itself and communicates with other slices on a secure basis minimizes the threat posed by cross-slice problems, securing network segments.
The integration of EAP protocols with identity management systems also makes it possible to implement centralized authentication policies and user identities in the huge network structure envisaged under 5G. This centralized approach effectively facilitates overall user management, authentication across devices and access points of various types as well as sensitive identity checks. It provides a concrete means to guarantee rigorous controls in every aspect of its use.
This lends 5G networks a strong authentication and encryption capability, which is driven by EAPs' innate adaptability. This enables the protocol to adapt when faced with emerging security threats and gives networks flexibility. In addition, EAP's flexibility would make it easier to incorporate security improvements in the future. By building on this foundation, 5G networks could continue protecting people and data over time by keeping a step ahead of ever-changing threats. When these security characteristics inherent in the indigenous system are included, EAP becomes a crucial component of securing 5G network deployments, focusing on various types of threats and building for the long-term future a foundation that is impervious to attack. Industrial IoT and EAPEAP protocols are instrumental in securing Industrial IoT (IIoT) networks by enabling:
Financial Sector ApplicationsEnhanced Authentication: EAP variants, including but not limited to EAP-TLS and EAP-TTLS, offer strong multi-factor authentication, which stringently authenticates user identities. Security is strengthened, as only authorized persons can access financial systems or engage in transactions safely. Safeguarding Your Exchanges: EAP-based encryption like EAP-TLS and PEAP guarantees a solid channel between your gadgets and the financial banking servers. It resembles having an invulnerable passage safeguarding your information from anybody attempting to sneak around or meddle. Defending Financial Information: These encryption abilities are vital safeguards for your monetary information. They're intended to repulse any efforts to penetrate your data, guaranteeing that your record subtleties and exchange points of interest stay classified. Battling Cyber Threats: EAP resembles an exceptionally versatile safeguard against various digital dangers. Consider it a utility belt where foundations can choose the right security efforts to fight specific attacks like phishing or denied access attempts. Also, it gets normal updates and improvements to remain strong against developing dangers. Meeting Guidelines: Consistent with guidelines like GDPR or PCI-DSS is imperative for monetary foundations. These EAP conventions offer the vigorous confirmation and encryption strategies expected to mark every one of the containers, safeguarding against any legitimate repercussions in the event of a break. Overseeing Client Identity: EAP improves things by bringing together client verification. This implies that just approved people can get to essential monetary frameworks, decreasing the gamble of inside breaks or unapproved access. At last, these conventions are the superheroes in the advanced world, defending your monetary data and exchanges from all points imaginable. ConclusionIn short, EAP is the foundation of security for existing wireless networks and the emerging 5G. Its flexibility and established authentication processes create a common security umbrella, which is indispensable for the secure operation of various devices on different network platforms. Whether in strengthening identity management, securing network slices, or counter-attacking emerging threats, EAP's built-in security characteristics are uniquely qualified to deal with the contemporary era. EAP will also continue to be a stability pillar of 5G as it extends, and can provide timely assistance with the continually mutating challenge of cybersecurity. Flexibility combined with absolute dependability makes EAP a certain choice for the future of wireless communications around the world.
Next TopicRole-Based Access Control (RBAC)
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









