Role-Based Access Control (RBAC)What is role-based access control (RBAC)?One technique for limiting network access based on the responsibilities of certain users within an organization is called role-based access control, or RBAC. RBAC, also known as role-based security, is a tool used by organizations to categorize access levels according to the roles and responsibilities of individual employees. Restricting network access is crucial for companies with a large workforce, contractors, or third parties that have access to the network, such suppliers and customers. This is because it may be difficult to adequately monitor network access. Businesses that use RBAC are better equipped to protect their sensitive information and vital apps. RBAC keeps users from accessing information that is irrelevant to them and makes sure they only access the data they need to do their duties. 
The rights that a person is allowed are determined by their job within the organization, guaranteeing that lower-level workers cannot access sensitive data or carry out high-level duties. The foundation of RBAC is the idea of roles and privileges. Factors like authority, skill, and accountability determine access. The employee may restrict access to the network and other resources, including files or programs. For instance, some programs or files may only have temporary access, whereas other files may be read-only in order to finish a job. Users may be classified by organizations as administrators, end users, or specialized users. Additionally, these jobs may overlap or provide distinct functions varying degrees of authorization. Effective procedures for implementing role-based access controlWhen adopting RBAC, organizations should adhere to a number of best practices, such as the following:
Benefits of Role-Based Access ControlThere are many security choices available, and choosing the best one for our business isn't always simple. Numerous well-established advantages of RBAC make it stand out from the competitors. 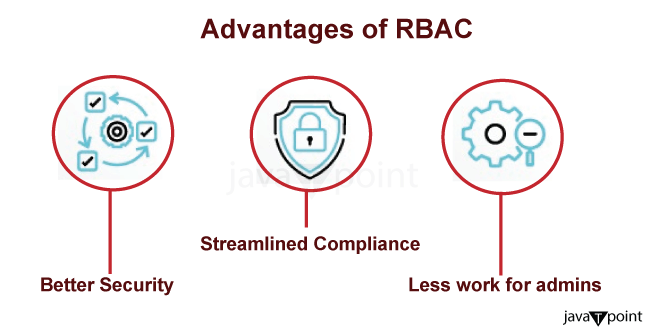
An RBAC framework is capable of:
RBAC versus ABACAlthough they both use access control techniques, role-based access control and attribute-based access control (ABAC) use different approaches. ABAC regulates access based on a mix of the following categories, while RBAC gives access permissions based on the responsibilities of users: 
RBAC is a predetermined role-based access control mechanism; in contrast, ABAC is more dynamic and provides more granular control. Organizations could utilize RBAC, for instance, to provide coarse-grained access control. For instance, all university professors should have access to Google for research purposes, and all contractors should have access to business email. However, businesses should employ ABAC when it comes to fine-grained access control or when they have to make judgements under certain circumstances. For instance, granting academics access to Google only in the event that they work in building X and instruct first-year students. RBAC examples includeA user may be assigned to a group or position by an organization. A user gains access to all of the permissions in a role group when they are added to it. An organization may choose to divide responsibilities among visitors, job-specific end users, and administrators. The following roles are examples of possible roles:
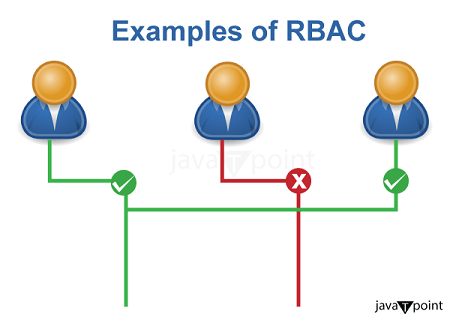
For example, software engineers will have access to the tools they need to do their work, but they won't have access to the data or resources that marketing or HR departments inside the same organization have. Similarly, marketing professionals will have access to the tools required for their work, but not software engineering or human resources tools. Each user's rights are based on their position and function inside the company. RBAC versus ACL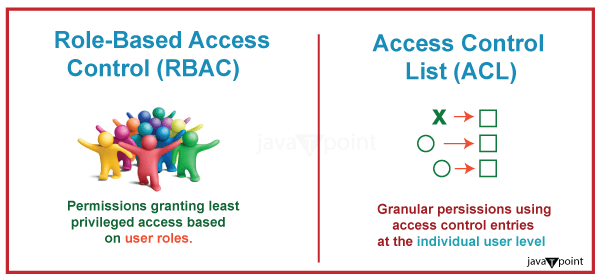
In terms of administrative burden and security, RBAC outperforms ACL for the majority of commercial applications. RBAC is more suitable for a company-wide security system with a supervising administrator, but ACL is better for establishing security at the individual user level and for low-level data. For instance, an ACL may allow write access to a certain file, but it is unable to control how a user could edit the file. Role-Based Access Control Permissions: What Are They?Permissions define a user's scope of access and actions inside the system. Permissions are the guidelines individuals abide by in accordance with the responsibilities we have delineated. The permissions should involve:
It's important to keep in mind that roles come first, not permissions. Establish the responsibilities of each position and apply permissions appropriately. Even if an employee's existing job limits them, don't let them ask for permission. If we start changing permissions one-by-one, the system might get quite complicated very fast.
Next TopicNetwork Enumeration Tools
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









