Install Nmap Ubuntu
Network mapper or Nmap is a network scanner made by Gordon Lyon (also popular by his pseudonym Fyodor Vaskovich). It is used to find services and hosts on a computer network by transferring packages and inspecting the responses.
Network mapper offers several features to examine computer networks, such as operating system detection and host service and discovery. These features are expandable by scripts that offer more leading vulnerability detection, service detection, and other features. It can adapt to many network conditions, such as congestion and latency during a scan.
Nmap began as a Linux utility, and it was moved to other systems such as BSD, macOS, and Windows. It is most famous on Linux, pursued by Windows.
Features of Nmap
Some of the important features of Nmap are listed and explained below:
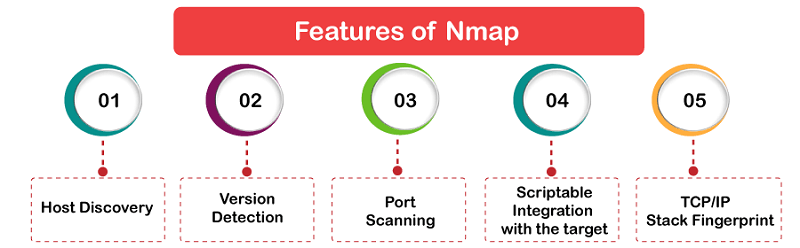
- Host discovery: It identifies hosts on any network. For instance, listing the hosts that answer ICMP or/and TCP requests or have a specific port open.
- Version detection: It interrogates remote devices by network services to examine the version number and application name.
- Port scanning: It enumerates the open ports on the target hosts.
- Scriptable integration with the target: It can be done with Lua programming language and NSE (Nmap Scripting Engine).
- TCP/IP stack fingerprint: It determines the hardware characteristics and operating system of network devices which are network activity observation-based of said devices
Nmap can give further details on targets such as Mac addresses, device types, and DNS names.
Typical Nmap uses as follows:
- Analyzing the security of a firewall or device by recognizing the network connections which can be done to or from it.
- Recognizing open ports on any target host in planning to audit
- Asset Management, network mapping, network inventory, and maintenance
- Analyzing the security of a network by recognizing new servers
- Producing traffic on a network to host, response time measurement, and response analysis
- Detecting and exploiting a vulnerability in any network
- Sub-domain and DNS query search.
User Interfaces of Nmap
Official GUI of Nmap, NmapFE, written by Kanchan originally for the 2.2 to 4.22 versions of Nmap. For the 4.50 version of Nmap (originally in the development series of the 4.22SOC version) and NmapFE was substituted by Zenmap, a fresh official GUI based on UMIT, designed by Adriano Monteiro Marques. Also, web-based interfaces are available that permit either analyzing Nmap outputs or controlling Nmap from a web browser like IVRE.
Output of Nmap
Nmap gives 4 possible formats of output. But all interactive outputs are saved to a file. These outputs can be employed by text processing applications, letting the user make customized reports.
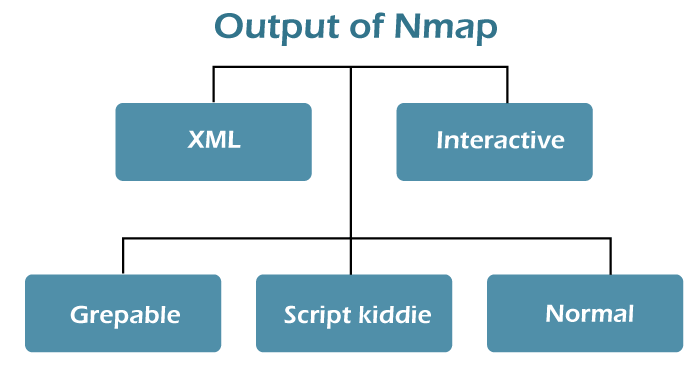
- XML
it is a format that can be further developed by XML tools. Also, it can be transformed them into an HTML report with XSLT.
- Interactive
updated and presented in real-time while the user executes Nmap through the command line. Several options can be enrolled at the time of the scan to provide monitoring.
- Grepable
output that's processed to line-oriented processing tools like awk, sed, or grep.
- Script kiddie
defined to be an amusing way for formatting the interactive output, substituting letters with their number representations visually alike. For instance, Interesting ports will be Int3rest1ng p0rtz. It is called Leet.
- Normal
the output as seen at the time of running Nmap through the comman
History of Nmap
First, Nmap was released in September 1997 in Phrack Magazine as an article with source code added. With contributions and the help of the community of computer security, development continued. Improvements included service fingerprinting, operating system fingerprinting, protocol support (such as SCTP, IPv6, etc.), additional scan types, code rewrites (C-C++), and new programs that are in addition to the core features of Nmap.
Major releases of Nmap, their dates, and description are mentioned as follows:
| Version |
Date |
Description |
| Nmap 2.00 |
12 December 1998, 23 years ago |
Nmap 2.00 is published, such as Operating System fingerprinting |
| NmapFE |
11 April 1999, 23 years ago |
It is a GTK+ front end and bundled with Nmap |
|
7th December 2021, 21 years ago |
Windows port |
|
28 August 2002, 20 years ago |
rewritten from C-C++ |
|
16 September 2003, 19 years ago |
The initial public version to add service version detection |
| Nmap 3.70 |
31 August 2004, 18 years ago |
core scan engine updated for the 3.70 version. The new engine is known as ultra_scan |
| Summer 2005 |
|
Nmap has chosen to participate in Google Summer of Code. Several features added second-generation operating system detection, Ncat, NSE (Nmap Scripting Engine), and Zenmap. |
| Nmap 4.50 |
13 December 2007, 14 years ago |
Nmap 4.50, the 10th-anniversary release, was published. Several features added Nmap Scripting Engine, 2nd-generation OS detection, and Zenmap. |
| Nmap 4.85BETA5 |
30 March 2009, 13 years ago |
An emergency version of Nmap 4.85BETA5, leveraging Nmap Scripting Engine to find Conficker infections |
| Nmap 5.00 |
16 July 2009, 13 years ago |
Added netcat-replacement Ndiff and Ncat scan comparison tool |
| Nmap 5.50 |
28 January 2011, 11 years ago |
Added Nping packet generation response time measurement and response analysis, including ICMP, UDP, and TCP probe modes. |
| Nmap 6.00 |
21 May 2012, 10 years ago |
Published with the full support of IPv6 |
| Nmap 7.00 |
9 November 2015, 7 years ago |
|
| Nmap 7.40 |
20 December 2016, 5 years |
|
| Nmap 7.70 |
20 March 2018, 4 years |
|
| Nmap 7.80 |
10 August 2019, 3 years ago |
|
| Nmap 7.90 |
3 October 2020, 2 years ago |
The new fingerprints permit better service/version and operating system detection. Three new NSE scripts, new payloads, and protocol libraries for host discovery, version detection, and port scanning. The 1.0.0 version of Npcap is the first completely stable release of the Windows raw packet sending/capturing driver. |
Legal issues of Nmap
A network mapper is a tool that can be used for discovering services active on internet connected systems. Potentially, it could be utilized for black hat hacking, like any other tool, as a precursor to getting unauthorized access to any computer system. Although, Nmap is also utilized by system and security administrators to use their networks for susceptibility (i.e., white hat hacking).
All system administrators can utilize Nmap to find unauthorized services or computers that don't break in.
License of Nmap
Originally, Nmap was distributed under the GPL (GNU Public License). In later versions, the authors of Nmap added specific interpretations and clarifications to the license in which they felt the GNU Public License was lacking or unclear. For example, the 3.50 version of Nmap particularly revoked the SCO Group license for distributing Nmap software due to their previews on the SCO-Linux controversies.
Beginning with the 7.90 version, Nmap transitions to a fresh custom NPSL license, dual-licensing versions 7.92, 7.91, and 7.90 under both new and old licenses. Many distributions of Linux consider the fresh license non-free.
Working of Nmap
Port scanning is a necessary part of Nmap. Users create a target list on a network that they wish to learn details about. These users do not need to recognize particular targets, which is nice because almost every administrator does not have a full image of everything that's using the several ports on their network. Rather, they compile a variety of ports to scan.
- Also, it is possible to scan every network port, but that would take time and consume a bit of bandwidth.
- In addition, depending on the passive defense types that are used on any network, like a massive port scan will likely encounter security alerts.
- Most people utilize Nmap in more restricted deployments or categorize different segments of their network for scheduled scanning.
- Also, users can manage the depth of all scans to set up a variety of targets to be scanned.
- For instance, a limited or light scan might give details that which port is open and which has not been opened by firewall settings.
- Additionally, more accurate scans could capture details about what type of devices are utilizing those ports, the OSes they are running, and the services that are running on them.
- Also, Nmap can find deeper information, such as the version of those detected services.
- It makes it a perfect tool to find vulnerabilities or assist with the efforts of patch management.
Managing the scans needed console commands, which means that training was needed. So, professionals can proceed to apply the console commands, making it a helpful tool for both novices and experts alike. Nmap can be helpful for protecting and optimizing information and networks when properly used. All return data transferred via ports scanned with Nmap is received and compiled via the program.
There are many key activities that almost all people utilize the tool to add accomplish. They contain:
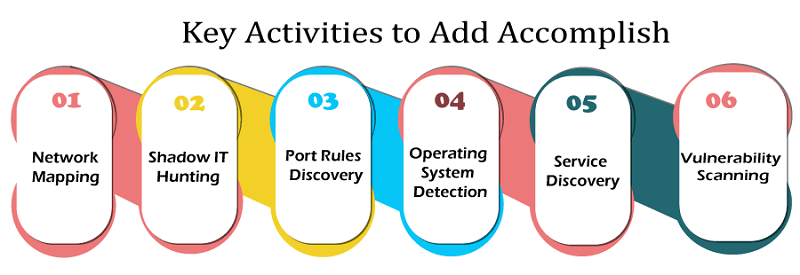
- Network Mapping: It is the main reason why Nmap was made and remained on top. Called host detection, Nmap will recognize the device types actively with scanned ports. It includes switches, routers, servers, and other devices. Also, users can check how these devices are linked and how they connect together to construct a network map.
- Shadow IT Hunting: It can be used to recognize things that shouldn't be there because Nmap can detect the location and type of devices on any network. These devices are known as Shadow IT due to their presence on the network is not authorized officially or sometimes may intentionally be hidden. This aspect can be dangerous because the devices aren't a part of a security program or audit.
For instance, if someone places any Xbox game server in a corporate network secretly, not only will that drain bandwidth potentially, but it could operate as a springboard for the attacks, especially if it is not managed with each latest security patch.
- Port Rules Discovery: If a port is closed or opened by something, such as a firewall, Nmap can easily detect it, even using a low-level scan. When programming firewalls, several IT professionals utilize Nmap to see their work. They can check if their policies are containing the desired effect and when their firewalls are properly working.
- Operating System Detection: Nmap can detect the types of operating systems active on discovered devices within a process known as OS fingerprinting. Generally, it returns details about the device vendor name (HP, Dell, etc.) and the operating system. We can even detect things such as the operating system patch level and the device's estimated uptime using a deeper Nmap scan.
- Service Discovery: It defines the ability to detect services that raises Nmap above a common mapping tool level. Users can encounter a deeper scan for finding out what roles detected devices are implementing rather than simply detecting that a device exists. It includes recognizing if they are operating as a mail server, a storage device, a database repository, a web server, or anything else. Also, Nmap can report on which particular application is running and what release of those applications are used relying on that scan.
- Vulnerability Scanning: Nmap isn't an embedded vulnerability scanning tool because it doesn't manage a database of any type of artificial intelligence or known vulnerability that could recognize potential threats. Although, organizations that constantly ingest security details from other sources or threat feeds can use Nmap to see their vulnerability to particular threats.
For instance, Nmap can be used to see if a program working on network assets currently meets those circumstances if a freshly uncovered vulnerability affects only a certain service or application running a previous software version. If anything is detected, then IT teams could presumably prioritize bringing those patched systems as quickly as possible for eliminating the vulnerability before any attacker coul
Installing Nmap in Ubuntu
Installing Nmap in Ubuntu with apt
We can install Nmap in Ubuntu with the help of the apt command.
- First of all, we need to update the system repository with the following command in the terminal window:
- Now, we will install Nmap using the below command:
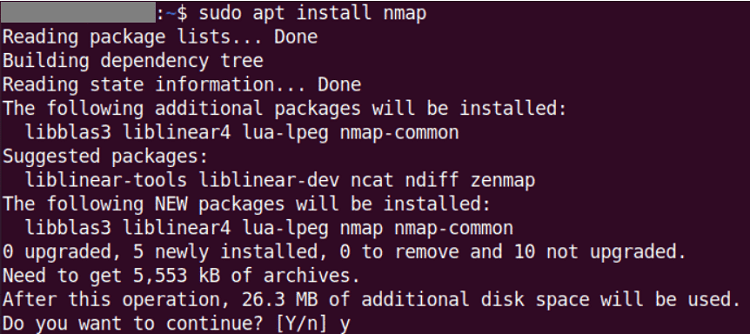
- We need to enter our sudo password, and we will be asked to confirm if we wish to continue with the installation process.
- We need to type the y button and click the Enter button to carry on.
- The installation process will take some time, based on our internet speed.
Installing Nmap in Ubuntu with Snap
Also, Nmap is available as a snap package in the Ubuntu operating system.
- We first need to install the Snapd tool on our system to install Nmap by snap.
- We will use the following command to get Snapd on our system:
- We will proceed to the second step once it is installed.
- We will use the following command in the terminal window to install the Nmap snap package:
- The installation process of Nmap will start, and the following result will be shown once completed.

- The above result displays Nmap has been installed on our system successfully.
|





 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now










